COINBASE CLOSE ACCOUNT
Bouquet of Cloud Services
BORROW AGAINST CRYPTO FOR CASH
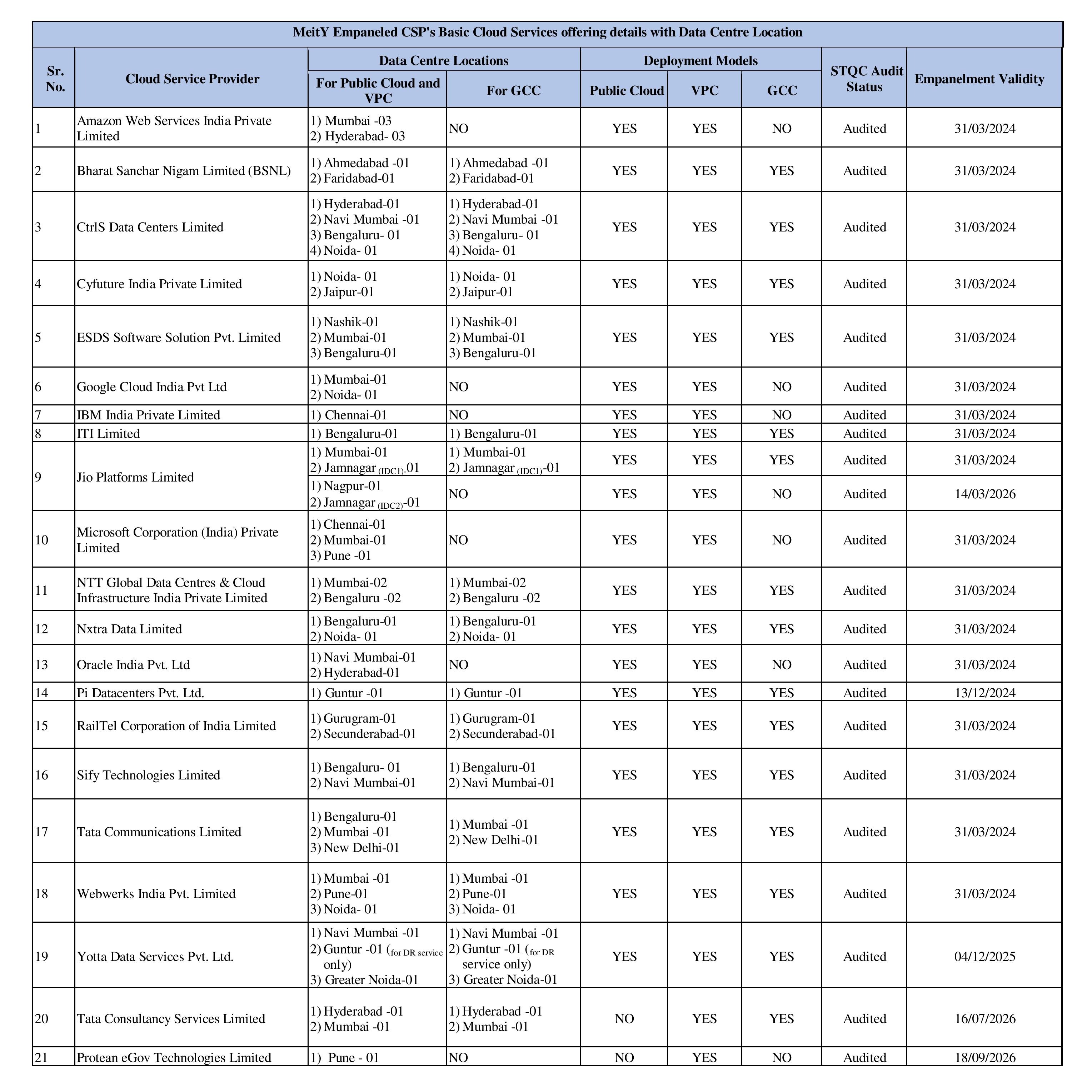
Basic Cloud Services
Public Cloud consisting of Compute Service, Storage Service, Network Service, Database Service, Security Service, Support Service
Register NowAdvanced Cloud Services
MPLS Connectivity, HSM, DDoS, TLS / SSL Certificate Management, Dual / Multi Factor Authentication, Monitoring Services, Office Productivity Suite, Analytics Services.
MENTORManaged Services
Managed Services consisting of Disaster Recovery as a Service and Backup as a Service
Register NowEmpanelment process
SMART WALLET COINBASE
- Empanelment is 24x7x365 opened
- The CSP can submit application for the proposed services from Bouquet of Cloud Services through this portal. For application submission : Click Here
- MeitY assess application basis Pre-Qualification criteria, Certification Compliances, Technical requirements, etc.
- STQC audit recommendation
- STQC audit of CSPs’ Data Centers & Cloud Services
- STQC informs MeitY on the status of audit
- Award of empanelment letter
- Listing of Cloud services & Data Center facilities of successful CSPs on MeitY’s website & other relevant platforms.
- Cloud services of successfully empaneled CSPs are onboarded on GeM platform
Cloud Guidelines
COINBASE LOANS
CASAS DE APUESTAS CON BITCOIN
Public Cloud
Public Cloud consisting of Compute Service, Storage Service, Network Service, Database Service, Security Service, Support Service
Virtual Private Cloud (VPC)
MPLS Connectivity, HSM, DDoS, TLS / SSL Certificate Management, Dual / Multi Factor Authentication, Monitoring Services, Office Productivity Suite, Analytics Services.
Government Community Cloud (GCC)
Government Community Cloud (GCC) consisting of Disaster Recovery as a Service and Backup as a Service.
FAQs
CRYPTO LEVERAGE
WITHDRAW COINBASECRYPTO BANK ACCOUNTTRANSACTION ID LOOKUP
SEI CRYPTO PRICEETHEREUM MINING RIGEASIEST CRYPTO TO MINE
Cloud computing is started in 1950s when mainframe computers came into existence. At that point, several users accessed the central computer via dummy terminals. The only thing these dummy terminals could perform was to enable users access the mainframe computer.
In 1970’s, IBM came out with an operating system (OS) named VM which was allowed for simultaneous operation of more than one OS. Guest OS could run on every VM, with their own memory and other infrastructure, making it possible to share these resources. This instigated the concept of virtualization in computing to gain popularity.
The 1990’s witnessed telecom operators begin offering virtualized private network connections, whose quality of service was good and at a lesser cost. This surfaced way for telecom companies to offer many users shared access to a single physical infrastructure.
The grid computing, which allowed major issues to be addressed via parallel computing; utility computing facilitated computing resources to be offered as a metered service and SaaS allowed subscriptions, which were network-based, to applications. Figure 1.1 describes the evolution of computing from mainframe to Cloud computing.
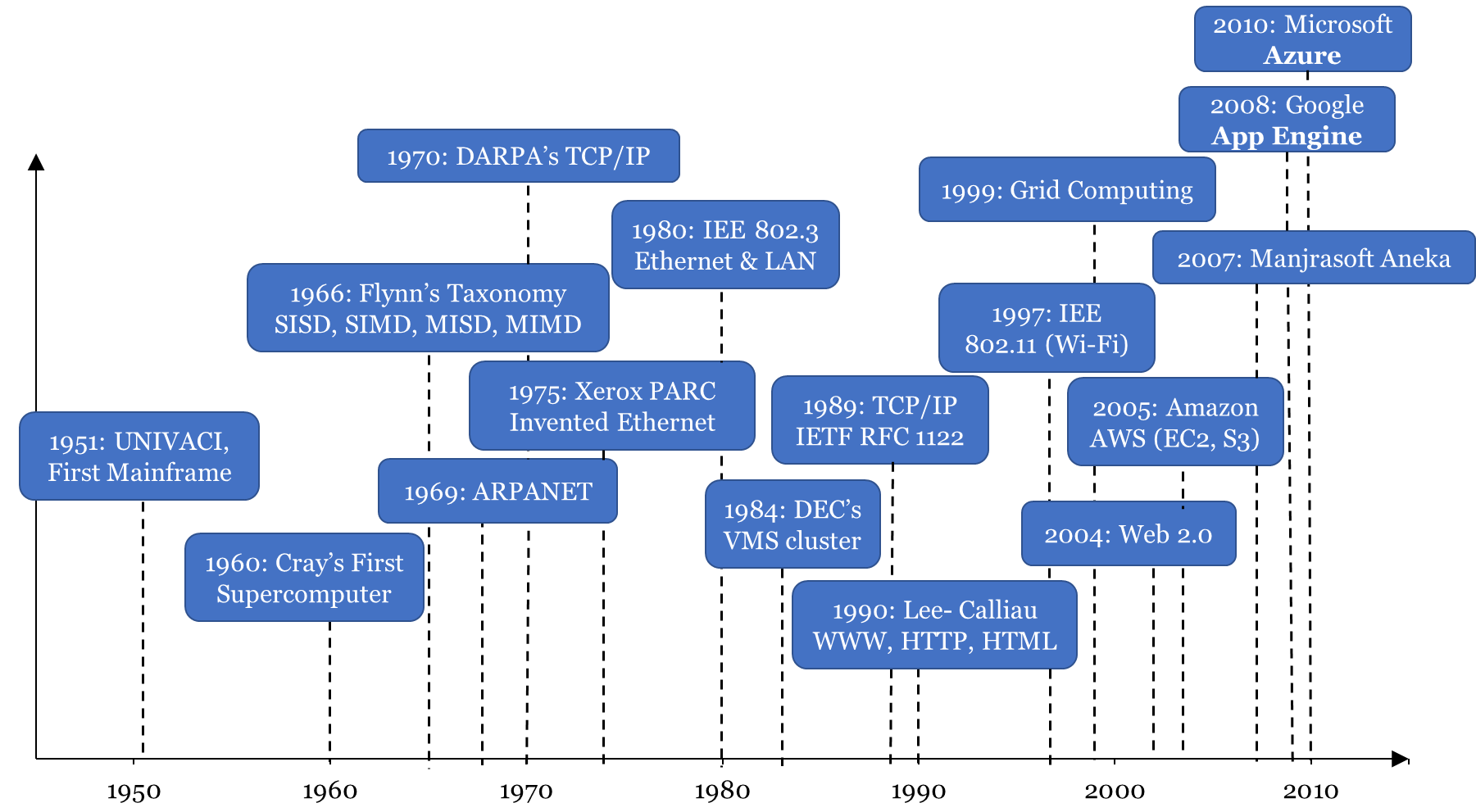
The evolution of distributed computing technologies, 1950s- 2010s
CRYPTO COM SHIBA INUCRYPTO MILLIONAIRE COUPLE BALI CRIME SCENECLOUD MINING CRYPTO
The term Cloud refers to a Network or Internet. Cloud is something, which is present at remote location. Cloud can provide services over network. Cloud Computing refers to manipulating, configuring, and accessing the applications online. It offers online data storage, infrastructure, and software.
300 BITCOINS TO DOLLARS$ROE CRYPTOAERGO CRYPTO
The phrase “Cloud Computing” originated in a collaboration project between IBM and Google. Cloud computing is a model, for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable resources (e.g. networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. Figure 1.2 shows the visual definition of Cloud computing given by NIST. The Cloud model has five essential characteristics, three service models, and four deployment models.
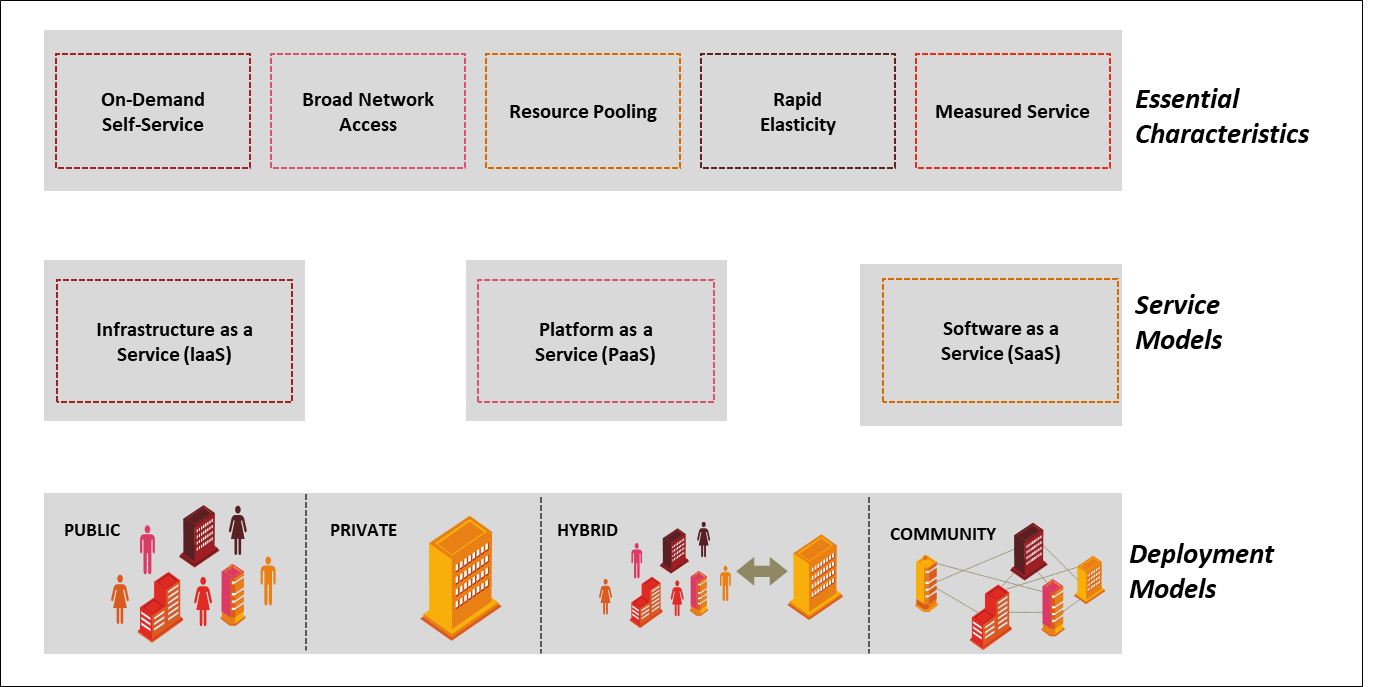
Cloud computing visual definition by NIST
Cloud computing means services provided through the internet. These services can be in the form of storage, application and hardware. The user can access these services any time anywhere without human interaction through internet. A pool of resources is created. Through virtualization these resources can be increased or decreased as per the requirement.
TESLA DOGECOIN NEWSCOINBASE VERIFY ACCOUNTBITCOIN SHORT ETF
The essential characteristics of Cloud computing as defined by NIST are given below:
- On-demand self-service: A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider.
- Broad network access: Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations).
- Resource pooling: The computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. There is a sense of location independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify location at a higher level of abstraction. Examples of resources include storage, processing, memory, and network bandwidth.
- Rapid Elasticity: Elasticity is the ability to expand or shrink a computing resource in real time, based on the real time computing requirements of users. Resources can be expanded or shrunk dynamically according to circumstances of the application and number of users.
- Measured Service: Measured Service refers to where Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g.-storage, processing, bandwidth, and active user accounts). Resource usage can be monitored, controlled, and reported, providing transparency for both the provider and consumer of the utilized service.
GDAX EXCHANGEREFER A FRIEND ON COINBASE50 CENT CRYPTO ARENA
The term software “multi-tenancy” refers to a software architecture in which a single instance of software runs on server and serves multiple tenants. Salesforce.com, Office 365 are some of the popular examples.
Using multi-tenancy, IT resources can be dynamically allocated and re-allocated based on consumer demands. Resource pooling allows Cloud providers to pool large-scale IT resources to serve multiple consumers. Resource pooling is commonly achieved through multi-tenancy technology, and therefore encompassed by this multi-tenancy characteristic.
WHERE TO BUY A SHIBABITCOIN STANDARDCRYPTO ETF NEWS
Once a Cloud is established, how it’s Cloud computing services are deployed in terms of business models can differ depending on requirements. The primary service models being deployed are commonly known as:
- Infrastructure as a Service (IaaS)- It contains all basic building blocks for Cloud IT and typically provides compute, network, and storage in virtual environment. In IaaS model the consumers can use fundamental computer resources such as processors, storage, and networking resources. An infrastructure provider (IP) provides the entire computing infrastructure “as a service”. Rather than purchasing servers, networking equipment and data storage, client rent the resources provisioned over a network.
- Platform as a Service (PaaS)- In this model, the computing platform is made available as a service. The client can build, test, and install their applications on the Cloud. The user (using the service) is responsible for the creation, updating and maintenance of the application. Like IaaS, customers of PaaS do not manage the underlying infrastructure, but control over the deployed applications. Typical examples of PaaS are IBM Bluemix, Google App Engine.
- Software as a Service (SaaS)- Software as Service (SaaS) provides a complete solution (infrastructure, platform and application) that is managed by the service provider. Under the SaaS model, the service provider is accountable for the creation, updating and maintenance of software, including the responsibility for licensing the software. The client frequently leases the software on a per usage basis. A good example could be web-based email running on a Cloud infrastructure, Google Apps etc.
ETHEREUM SEPOLIA FAUCETPRIME CRYPTO PRICEUSDT TO CAD
Depending upon the way Cloud services are provided to users, different Cloud deployment models are:
- Public Cloud: The Cloud infrastructure is provisioned for open use by public on internet. It is owned, maintained, and operated by a CSP. The CSP is responsible for the creation and maintenance of the public Cloud and its IT resources. Applications on public Cloud are either created in the Cloud environment or migrated from an existing infrastructure to take advantage of the benefits of Cloud computing. Cloud-based applications can be built on low-level infrastructure pieces or can use higher level services that provide abstraction from the management, architecting, and scaling requirements of core infrastructure. Public Cloud exists on CSP premises. Some popular CSP’s are AWS, Microsoft Azure, Google App Engine, etc.
- Private Cloud: Deploying resources on-premises, using virtualization and resource management tools, is called “Private Cloud”. It may be managed either by the Cloud Consumer organization or by a third party and may be hosted on the organization’s premises or outsourced to a hosting company (i.e., outsourced private Clouds). Some of the popular software that is used for establishing Private Cloud are Microsoft System Centre, VMWare, vCloud, Openstack, etc. Openstack is an opensource software with distributions and support from IBM, Redhat, HP, etc.
- Community Cloud: Community Cloud is shared Cloud which supports a specific community that has shared concerns (e.g., mission, security, policy, and compliance considerations). Like private Clouds, a community Cloud may be managed by the organizations or by a third party and may be implemented on customer premise (i.e., on-site community Cloud) or outsourced to a hosting company (i.e., outsourced community Cloud).
- Hybrid Cloud: Hybrid Cloud consists of combination of both private Cloud and public Cloud features. The Cloud infrastructure is a composition of two or more distinct Cloud infrastructures (private, community or public) that remain unique entities, but are bound together by standardised or proprietary technology that enables data and application portability (e.g., Cloud bursting for load balancing between Clouds).
WHY CRYPTOS ARE FALLINGBTC USDT TRADINGVIEWCIPHER DECODER
Cloud Bursting is a model in which application running in private Cloud bursts/scales automatically into a public/community based on scalability needs. This typically happens for the additional load balancing needs of application/web server. After the reduction in usage, the scale down can also happen automatically.
NEW BITCOIN CASINOSCOINMAHOW DO YOU CASH OUT ON COINBASE
A traditional application is a n-tier/ monolithic application architecture that generally consists of database, application and web servers that are tightly coupled with infrastructure and relies on it for providing availability. A Cloud native application is one that uses open, common standards, is dynamic in nature and is highly scalable with no dependencies on the underlying infrastructure. Cloud-native or third platform, Cloud services have ushered newer ways of designing, partitioning, scaling, testing, and deploying applications. Modern applications are built around Cloud services with application program interface (API) calls, shared infrastructure and with quick deployment process. In contrast, legacy and other client-server applications are built assuming ownership of an entire OS. These applications are shoehorned into shared infrastructure via hypervisors and VMs; in other words, they can run on, but aren’t built for, the Cloud.
LATEST SHIBA INU NEWSKITCO BITCOIN CHARTIS BINANCE AVAILABLE IN TEXAS
The common benefits gained from Cloud system implementation are:
- Efficiency / Cost reduction: By using Cloud infrastructure, one doesn’t have to spend huge amounts of money on purchasing and maintaining equipment. This reduces capex costs. Also, one did not have to invest in hardware, facilities, utilities or building out a large data centre. Cloud also helps in reducing cost related to downtime.
- Data Security: Cloud enables many security features that guarantee that data is securely stored and handled. Cloud Service Providers implement baseline protections for their platforms and the data they process, such authentication, access control and encryption.
- Scalability: Using Cloud enables enterprise to efficiently and quickly scale up/down their IT departments according to business demands.
- Accessibility: Cloud allows to access information anytime, anywhere, making life easier.
- Mobility: Cloud technology allows people to access critical data and software from anywhere, anytime with the help smartphones and devices, which ensures that no one is ever left out of the loop.
- Control: Cloud enables one complete visibility and control over the data. One can easily decide which users have what level of access to what data.
BEST CRYPTOCURRENCY TO BUY CHEAPPOLYGON BLOCKCHAIN EXPLORERXRP HAS OVERTAKEN USDC IN TERMS OF MARKET CAP
CRYPTO POLICYCRYPTO SCHEDULEBITSTAMP LEVERAGE
The Cloud computing architecture consist of four layers:
- Consumer/User Layer: The consumer/user initiates the connection to the Cloud. The consumer can be any device such as laptop, desktop tablet, and smartphones deployed.
- Network Layer: The whole Cloud infrastructure is dependent on this connection where the services are offered to the consumers. This could be internet, MPLS/leased lines for public, community and hybrid Cloud. In the case of private Cloud, the connectivity may be provided by a local area network. Usually, when accessing the public or private Cloud, the users require minimum bandwidth, which is sometimes defined by the Cloud service providers.
- Cloud Management Layer: This layer consists of software that is used to manage the Cloud. This is the orchestration layer which allows provisioning and managing of Cloud resources through console. This software allows resource management (scheduling, provisioning, etc.), optimization (server consolidation, load balancing) and internal Cloud governance.
- Hardware layer: This layer consists of hardware resources such as Servers (compute and RAM), Storage devices, Clusters, and Datacentres for all types of Clouds.
WE BULL CRYPTOCRYPTOCOINTRACE COM REVIEWCOINMART
The Fig 2.1 represents an overview of NIST Cloud computing reference architecture, which identifies the major actors, their activities and functions in Cloud computing. The diagram depicts a generic high-level architecture and is intended to facilitate the understanding of the requirements, uses, characteristics and standards of Cloud computing.
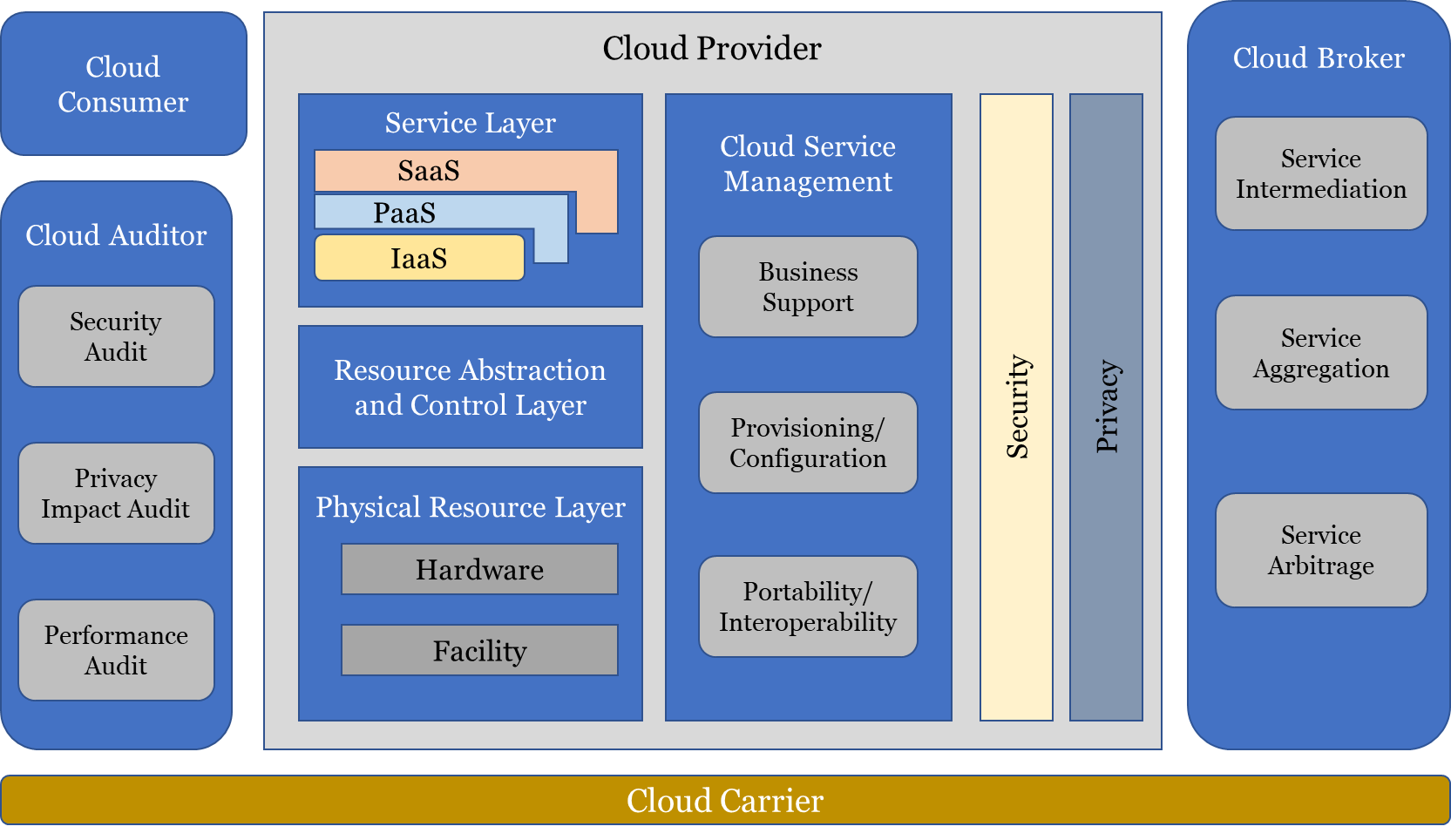
Cloud Computing Reference Architecture
TETHERING 7 LITTLE WORDSHOW LONG DOES ID VERIFICATION TAKE ON COINBASEWHERE IS THE CRYPTO ARENA
The Cloud architecture consists of five elements:
- Cloud Consumer: A person or organization that maintains a business relationship with and uses service from CSPs.
- Cloud Provider: A person, organization, or entity responsible for making a service available to interested parties.
- Cloud Auditor: A neutral third party that can conduct independent assessment of CSPs and Cloud services considering their information system operations, performance, security of Cloud and many other parameters to provide Cloud Evaluation as a Service (CLEaaS).
- Cloud Broker: An entity that manages the use, performance, and delivery of Cloud services, and negotiates relationships between Cloud Providers and Cloud Consumers.
- Cloud Carrier: An intermediary that provides connectivity and transport of Cloud services from CSPs to Cloud consumers.
CRYPTO CONVENTION NASHVILLEWHAT TIME WILL TRUMP SPEAK AT THE BITCOIN CONFERENCESTAKE ETH ON COINBASE
The role of each layer in Cloud reference architecture is:
- Service Management: It refers to the composition of system components to support the Cloud provider activities in arrangement, coordination, and management of computing resources in order to provide Cloud services to consumers.
- Service Layer: This layer defines interfaces for Cloud consumers to access the computing services. Access interfaces of each of the three service models are provided in this layer. It is possible, though not necessary, that SaaS applications can be built on top of PaaS components and PaaS components can be built on top IaaS components.
- Resource Abstraction and Control layer: This layer contains the system components that Cloud provider uses to provide and manage access to the physical computing resources through software abstraction. Examples of resource abstraction components include software elements such as hypervisors, virtual machines, virtual data storage, and other computing resource abstractions. The control aspect of this layer refers to the software components that are responsible for resource allocation, access control, and usage monitoring.
- Physical Resource Layer: This layer includes hardware resources, such as computers (CPU and memory), network (routers, firewall, switches, network links and interfaces), storage components (hard disks) and other physical computing infrastructure elements. It also includes facility resources, such as heating, ventilation, and air conditioning (HVAC), power, communications, and other aspects of physical plant.
SHIBA INU CALCULATOR TO USDRNT CRYPTOTANGEM CRYPTO WALLET
- Security Audit: Systematic evaluation of a Cloud system by measuring how well it conforms to a set of established security criteria.
- Privacy-Impact Assessment-Systematic Assessment of a Cloud system by measuring how well it conforms to a set of established privacy-impact criteria.
- Performance Audit: Systematic evaluation of a Cloud system by measuring how well it conforms to a set of established performance criteria.
These audits provide information that could be used for internal/external compliance requirements.
COINBASE AVAILABLE TO SEND IN 7 DAYSBITWISE CRYPTOMICA CRYPTO
Cloud service management includes service-related functions that are necessary for the management and operation of those services required by Cloud consumers.
- Business Support: Involves the set of business-related services dealing with consumers supporting processes. It includes accounting, billing, reporting, and auditing
- Provisioning/Configuration: This includes automated tools for rapid development of Cloud systems for consumers, adjusting configuration and resource assignment, monitoring and reporting on resource usage.
- Portability/Interoperability: Consumers are interested in Cloud offerings that support data and system portability and service interoperability. This is useful in hybrid Cloud environment, where the consumer may wish to change the allocation of data and applications between on premise and off-premises locations. For moving application from one Cloud to another, user departments should ensure that CSP does offer them ability to take the data out of Cloud in non-proprietary format.
- Security: Security is an important aspect of the architecture that spans across all layers of the reference model, ranging from infrastructure security to application security. Therefore, security in Cloud computing architecture is a shared responsibility between user department and CSP. CSPs security implementations on authentication, authorisation, availability, confidentiality, identity management, integrity, audit, security monitoring, network security, logging and alerting, encryption and data protection, incident response, and security policy management need to be verified and validated.
- Privacy: Cloud Providers should protect the assured, proper, and consistent collection, processing, communication, use and disposition of personal information (PI) and personally identifiable information (PII) in the Cloud. Such encryption technologies can be used for sensitive and personal data – at rest (in databases/storage) or while in movement (over networks, between applications etc.)
CRYPTO IRAHASH AI CRYPTOETHERESCAN
Cloud architecture provides a large pool of dynamic resources that can be accessed any time whenever there is a requirement, which is not provided by the traditional architecture. In traditional architecture, it is not possible to dynamically allocate a resource (VM, storage, etc.) with the rising demand of infrastructure and services. Cloud architecture provides scalable properties to meet demand of infrastructure and provide on-demand access to the user.
BINANCE HOLDINGSSCORPION CASINO CRYPTO PRICEO2T CRYPTO PRICE PREDICTION 2030
BITCOIN PARKWHEN WAS THE UNI TOKEN BY UNISWAP LAUNCHEDDOES FREQTRADE SUPPORT COINBASE
Cloud applications are best deployed as a collection of Cloud services, or APIs. At its essence, it is a service based or service-oriented architecture. While developing an application architecture for the Cloud, following steps should be noted and if applicable adhered to:
- i. Loose Coupling of service
- ii. Service Granularity
- iii. Decouple the data
- iv. Intercommunication between application components
- v. Model and design for performance and scaling
- vi. Security within applications
This is a fundamental concept of Service Oriented Computing. It ensures that applications components are treated individually, and dependencies are reduced. It further ensures that addition, removal, failure, or update of one component has a minimum impact on other components. Thus, it is always recommended to develop components separately and defining their integration/ interaction mechanism in a separate component.
Each service operation should ideally perform single transaction to simplify error detection, error recovery, and simplify the overall design. Each service operation should map to a single business function, although if a single operation can provide multiple functions without adding design complexity or increasing message sizes, it can genetically reduce implementation and usage costs
Since private and public Clouds are complex distributed systems that work best with application architectures that break out processing and data into separate components. By decoupling, the data can be stored and processed on any public or private Cloud instance. In such cases latency may occur, so it is recommended to use caching systems. These provide additional database performance by locally storing commonly accessed data, thereby reducing all database read requests back to the physical database.
Note: For systems which are constantly reading new data don’t benefit much from caching systems.
Application components that communicate with each other continuously may lower the performance of the overall application. In order to improve the performance combining the communications into a single stream of data, rather than constantly sending messages is the best practice
Firstly, a test case should be built that represents how an application behaves under an increased load. While the traffic increases, the number of web server and associated database instances may have to be increased to handle any additional load. This can help to understand the process to scale the application by automatically increasing resource on the instances or load balancing. In some cases, Cloud service providers offer auto-scaling capabilities, where provisioning occurs automatically. In this manner, it becomes easier to understand the application"s workload profile and defining the path to scaling the application.
Developing solution architectures that focus on mature Identity and Access Management capabilities can reduce security costs for organizations.
FREE BITCOIN PROMO CODE 2024BITSTWASH TRADING CRYPTO
Vertical scaling provides more resources to a single computational unit, whereas horizontal scale out provides additional computational unit and runs them in parallel. Vertical scale up provides a provision to move a workload to other system that doesn’t have workload, whereas horizontal scaling splits the workload among various computational units.
SELL MONEYAVT CRYPTOCOINBASE FUTURES
- Virtualization: Creation of virtual resources from the physical resources such as compute, storage, network, etc.
- Utility Computing: Is based on Pay per Use model. It offers computational resources on demand as a metered service.
- Grid Computing: Refers to distributed computing in which a group of computers from multiple locations relate to each other to achieve common objective. These computer resources are heterogeneous and geographically dispersed.
WHEN WILL THE BITCOIN BILL BE VOTED ONCRYPTO LOKO CASINO $200 NO DEPOSIT BONUS CODESZACH BRYAN CRYPTO COM ARENA 4 JUN
The comparison between Clouds and Grids is provided in the table below:
|
Characteristics |
Grids |
Clouds |
|
Population |
High-end computers (servers, clusters) |
Commodity computers and high-end servers and network attached storage. |
|
Size/Scalability |
Scalability is normal |
Scalability is high |
|
Node OS |
Any standard OS (dominated by Unix) |
A hypervisor on which multiple VMs run with different Operating Systems |
|
Ownership |
Multiple |
Single |
|
Interconnection Network/Speed |
Mostly Internet with high latency and low bandwidth |
Dedicated, high-end with low latency and high bandwidth. |
|
User Management |
Decentralized and virtual organisation (VO) based |
Centralized or can be delegated to third party. |
|
Resource Management |
Distributed |
Centralized/Distributed |
|
Failure Management |
Limited (often failed tasks/applications are restarted) |
Strong support for failover and content replication. VMs can be migrated from one node to other |
NIMBLE CRYPTOCOINBASE GIFTCARDCASA CRYPTO
CRYPTO NEWS SHIBA INUCOINBASE USDC TO USDCOIN BA
Types of virtualization in Cloud Computing are:
- Operating System Virtualization: In this the virtual machine software installs in the operating system of the host rather than directly on the hardware system. The most important use of operating system virtualization is for testing the application on different platforms or operating system.
- Server Virtualization: In server virtualization, the software is directly installed on the server system and use for single physical server can divide into many servers on demand basis and balance the load.
- Hardware Virtualization: Used in server platform as it is flexible to use Virtual Machine rather than physical machines. In hardware virtualizations, virtual machine software installs in the hardware system and then it is known as hardware virtualization. It consists of a hypervisor which use to control and monitor the process, memory, and other hardware resources.
- Storage Virtualization: In storage virtualization in Cloud Computing, a grouping is done of physical storage which is from multiple network storage devices this is done so it looks like a single storage device. It can implement with the help of software applications and storage virtualization is done for the backup and recovery process.
STAKE ETH ON COINBASECLOSE A COINBASE ACCOUNTUSD TO DOGE
Cloud can be present without virtualization, although it will be difficult and inefficient because the Cloud relies on concept such as “Pay for what you use” and “Indefinite availability-use as much you want”. These concepts are possible only if we have lot of flexibility (scale in/out) and efficiency in the back end. This flexibility and efficiency are readily available/possible only through virtualization. However, most Cloud applications-specially in a public Cloud- will be deployed on the Operating System (Windows/Linux) layer or on the Platform Layer (J2EE, .NET, etc.) and the underlying virtualization technology or the hypervisor would not be visible to the applications.
100 USD TO BITCOINBAINASWHERE CAN I BUY BITCOINS WITH CASH
TXT CRYPTO ARENABITSTAMP REVIEWCENTRA CARD CRYPTO
- It helps in saving cost and can be maintained easily at less cost
- It allows multiple operating systems on one virtualization platform
- It removes the dependency of heavy hardware to run the application
- It provides consolidating servers to increase resource utilization
PEIPEI CRYPTOAPE STORE CRYPTOEFT BITCOIN FARM WORTH IT
- 1) Type I or bare metal
- 2) Type II or hosted hypervisor
Type I hypervisor directly runs on the host hardware, creates the virtual machines, and monitors the operating systems. The additional overhead of communicating with the host OS is reduced and offers better efficiency. This type of hypervisor is used for servers that handle heavy workload and require more security. Examples include Microsoft Hyper-V, VMware ESXi, Citrix Xen Server, etc.
Type II hypervisor runs on the top of the host operating system and creates Virtual Machines (VM) and runs guest operating systems. This host OS is also known as physical host, which has the direct access to the underlying hardware. The major problem of this approach is the failure/crash of host OS, results in crashes of all VMs. Hence, it is recommended to use Type II hypervisor only in Desktop’s systems, where efficiency is less critical. Examples include VMware Workstation, Oracle Virtualbox and KVM.
A summary of hypervisors:
|
Hypervisor |
Vendor |
Type |
License |
|
Xen |
University of Cambridge Compute Laboratory |
Type I |
GNU GPL v2 |
|
Vmware ESXi |
Vmware, Inc. |
Type I |
Proprietary |
|
Hype-V |
Microsoft |
Type I |
Proprietary |
|
KVM |
Open Virtualization Alliance |
Type II |
GNU GPL |
|
Vmware Workstation |
Vmware, Inc. |
Type II |
Shareware |
|
Oracle Virtual Box |
Oracle Corporation |
Type II |
GNU GPL v2 |
Summary of Hypervisors
WHEN WAS CASPER FOUNDED CRYPTOBITWISE CRYPTOSSHIB COIN
The number of virtual machines that can be deployed on the server depends on the server capacity (memory, processor, speed, etc.) and application resources requirements for the virtual server. The higher capacity equipment and lower their consumption, the greater the number of virtual machines can be placed. Conversely, a small capacity and high consumption of resources means that a smaller number of virtual machines can be placed on a single physical server.
CEX EXCHANGE UKCOINBASE VERIFY IDENTITYDOGE COIN PRICE FROM APRIL 24TH 2021
Yes, some of the features like ‘live cloning’ can spin up an exact replica of the VM instantly on another host, without switching off the original, thereby migrating it live with no downtime required. However, this feature may not be available with all the CSPs and with all their offerings.
SHIB BURN SHIBARIUMIS IT TOO LATE TO INVEST IN BITCOINCRYPTO ARENA PREMIER SEATS BENEFITS
کارت USDT ON TONCOINBASE ACCOUNT RESTRICTED4 ETHER TO USD
Clouds are connected through APIs in a technical sense and through partnerships in a business sense. Private Cloud vendors sometimes offer public Cloud services or public Cloud vendors often collaborate with private Cloud vendors to create hybrid Clouds. These hybrid Clouds are inter-connected using secure VPN technologies to ensure that the on-premises infrastructure and the off-premise, Cloud infrastructure operate as if they are within the same corporate network.
11 000 EUROS TO DOLLARSSTAPLE CENTER LOS ANGELES CA ADDRESSBLACKROCK AND BITCOIN
Some of the emerging technologies either Cloud-based or highly interoperable with the Cloud are:
- Containers: Unlike the virtual machine popularized by VMware, which must hold the entire OS, containers wrap a piece of software in a capsule that’s like a lightweight “computing suitcase.” The container carries the software itself and only the essentials needed (libraries and configuration files) to travel among computing environments. Containers reduce the overhead of Virtual Machine Guest OS and bundle only those OS components that are required for microservice or the application.
- Microservices breaks these unwieldy monolithic apps into several smaller, joined services, or “modules.” It uses a modular approach, with small teams updating modules as needed, independent of the full hulking application. Microservices enables continuous delivery of freshly updated software. Like serverless, it allows app development to move at the faster speed necessitated by the Cloud era.
- Serverless: Serverless PaaS which enables high-performance business data processing without the need for expensive servers. As the Cloud service provider manages all computing resources, it becomes easy for business owners to “build out their Cloud-based systems.” The biggest benefit of serverless: the Cloud host executes “snippets of code” without involving developers.
- Edge Computing: allows real-time analytics to occur very close to the source of the in-stream IoT data
- Artificial Intelligence and machine learning: Computer systems are becoming more intelligent, using machine learning to analyse data it receives and make automated decisions, diagnoses, and responses based on its analysis. Plenty of Cloud computing solutions are powered by AI and machine learning systems themselves, and public Cloud environments extend those capabilities to the users.
- Internet of Things: More and more devices are connecting to the Internet every day, and it’s gone beyond traditional electronics like computers and phones. The Internet of Things (IoT) allows more types of devices to connect to other systems. Providing the computing power for these devices can be difficult, however, and managing them all is infuriating without a centralized tool. Cloud environments allow for IoT devices to operate smoothly by allowing for them to have the resources necessary to run.
CRYPTO EXCHANGES IN CANADABITCOIN FARM TARKOVRENQ CRYPTO
The Government’s focus on digitalizing governance under the “Digital India” campaign has led to an increase in computing resource requirements for numerous projects. To meet the existing Infrastructure requirements and to reap benefits provided by the Cloud computing, Government Departments are now more inclined towards adopting Cloud.
Nowadays, Cloud technology is enabling practices such as DevOps to simplify and speed up the application development process. The near real-time response to Department needs with benefits of Cloud would enable the government departments to efficiently deliver internal and citizen centric services leading to increase in adoption of Cloud-based infrastructure, platforms, and applications. Cloud enables Departments to operate more efficiently, reducing up up-front capital costs while providing flexibility in data storage, processing, and other functionalities. As Government Departments are migrating existing applications to the Cloud and developing new capabilities/applications on the Cloud, understanding, and designing Cloud deployment architectures with elements of security and management have become crucial while adopting Cloud.
In this regard, an architecture is being proposed which shall be referred to as ‘Government of India Cloud Reference Architecture (GI CRA)’ The reference architecture has been designed using globally prescribed frameworks (addressing security and privacy requirements) and is based on the regulatory and compliance needs for application deployments in the Cloud. The design of GI CRA is intended to illustrate and understand the various Cloud services in the context of Cloud computing and to provide a technical reference to Government Departments to understand, categorize and compare Cloud services. The GI CRA comprises of various building blocks and their relationships with each other which ultimately shape to form up a Cloud setup.
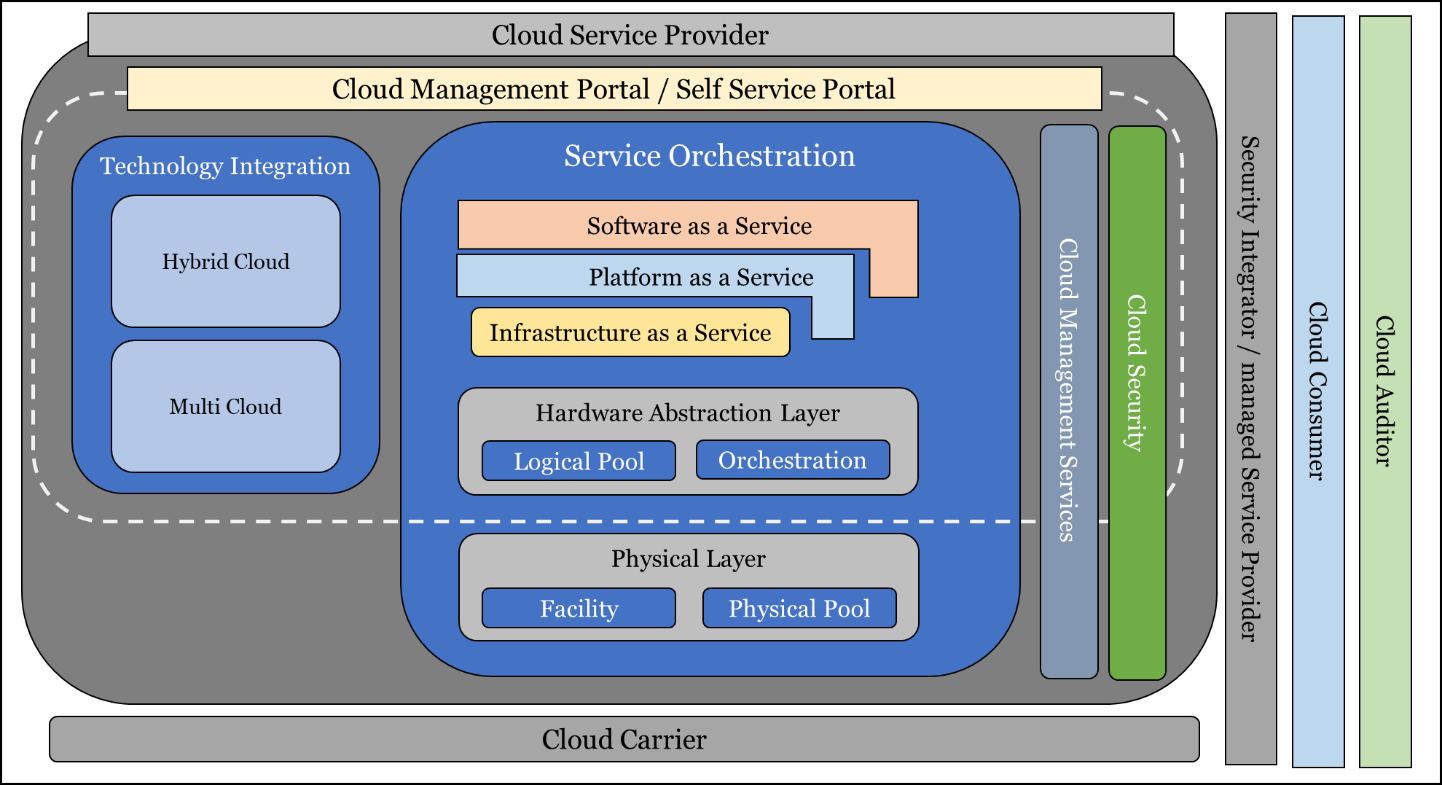
GI Cloud Computing Reference Architecture
The figure above details the various building block which make up the GI Cloud Reference Architecture. This Reference architecture may be leveraged as a framework to build/design Cloud deployments/environment.
WHERE IS CRYPTO COM BASEDCRYPTO MILLIONAIRE COUPLE MURDERED IN BALIクリプトドットコムアリーナ
GI CRA comprises of the following essential layers/components/entities:
- Cloud Service Provider
- Service Orchestration
- Cloud Management/Self-service Portal
- Cloud Service Management
- Cloud Security Architecture
- Cloud Carrier
- Managed Service Provider
- Cloud Consumer/Government Departments
The GI CRA also comprises of an Integration layer which may be utilized for Cloud practices like Hybrid Cloud, Multi-Cloud etc.
The GI CRA layers/components/entities are described as below:
|
Layer |
Description |
|
Cloud Consumer |
User or consumer of GI Cloud services i.e. Government Departments at Centre and State level, Citizens |
|
Cloud Service Provider |
Entity responsible for operating Cloud environment and make GI Cloud services available to Cloud consumers |
|
Managed Service Provider |
Entity responsible for delivering and managing Cloud services for the Cloud consumer |
|
Cloud Carrier |
Intermediary responsible for connectivity and transport of Cloud services from Cloud Service Providers to Cloud Consumer |
|
Service Orchestration |
Layer covering the management of physical DC facility, IT hardware infrastructure, hardware abstraction layer (Hypervisor) and provisioning of three Cloud service models IaaS, PaaS & SaaS |
|
Cloud Management Platform/ Self Service Portal |
Single pane of glass from where Cloud consumer or Government Department can provision, manage, and terminate services themselves |
|
Cloud Service Management |
Responsible for the smooth execution of Cloud build & operate. Includes Cloud implementation, operations & maintenance services |
|
Cloud Security Framework |
Comprehensively address all the security related aspects. Defines guidelines on security addressing the various challenges, risks and for prescribing the approach for mitigating the risks |
Layers in Cloud Computing
CRYPTO DEFI WALLETBABY GROK CRYPTOWILL ETHEREUM SURPASS BITCOIN
The GI Cloud Reference Architecture is intended to facilitate the understanding of operational intricacies in Cloud computing with focus on “what” Cloud services provide. Government of India has referenced the Conceptual Reference Model of National Institute of Standards and Technology’s (NIST). A requirement to design a GI Cloud Reference Architecture arose to standardize on the nomenclature of terms, various actors and their roles & responsibilities in the GI Cloud ecosystem.
The GI Cloud Reference Architecture has been designed to assist the Government Departments to build their Cloud deployment architecture with components, activities and actors as relevant in the GI Cloud ecosystem. The Reference architecture is a vendor neutral architecture and has been designed by adopting widely used and recognized Cloud reference architecture and their components.
Note: All the aspects on the proposed Cloud Reference Architecture have been covered in detail in the GI Cloud Reference Architecture document, available on the MeghRaj webpage of MeitY’s website.
COINBASE ACCOUNT CLOSEDBITCOIN SOLO MININGFAUCETS CRYPTO
CRYPTO MINING APPDOGECOIN CLICKERBINANCE WEB3
Some of the advantages of moving to Cloud are:
- Operational costs: No need to pay for the equipment, maintenance and hardware upgrade. Access to a multitude options and the opportunity to experiment at a low price, without capital expenditures.
- Elasticity and pay-per-use: The elastic environment model of the Cloud is usage-based, which makes it possible to easily scale and increase computing power on-demand as well as reduce hardware resources when they not needed.
- Risk mitigation and maximum availability: Quick disaster recovery and maximum resilience and uptime.
- Security: CSPs invest far more resources to secure their applications and client data.
- Big Data and advanced analytics: With the Cloud, it is possible to store, access and analyse almost unlimited volumes of data.
BITTENSOR NAD THE NEST AI CRYPTO TO INVEST INBITCOIN ETF TAX IMPLICATIONSTRADING IN COINBASE
The key difference between the Cloud and traditional datacentres is that traditional datacentres are usually on-premise at an organisation’s office location. Cloud refers to datacentres that are managed by a Cloud Service Provider (CSP) from a central location(s) and are accessed and managed over the internet rather than an internal network.
CRYPTO TRADING TOOLSBTC行情CRYPTO MINING RASPBERRY PI
Gain full understanding of:
- Organisation’s drivers/motivation to move to the Cloud.
- Whether Cloud computing works for your business model?
- Whether your organisation have the expertise to implement and manage estate in the Cloud?
Some organisations implement a ‘lift and shift’ approach to the Cloud, which is not always the right approach. When moving to the Cloud, core business processes and policies will likely need to change, so an understanding, documentation and risk assessment of these policies is recommended.
CENTRALIZED VS DECENTRALIZED CRYPTOSHIBA DOGE PRICEWHEN IS THE NASHVILLE BITCOIN CONFERENCE
The Government of India has paved the way for mass adoption of Cloud services by the Government and Public sector organizations by empanelling the CSPs with Ministry of Electronics & Information Technology (MeitY). The CSPs are empanelled to offer Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS) under the three Cloud Deployment models namely, Public Cloud (PC), Virtual Private Cloud (VPC) and Government Community Cloud (GCC).
NON KYC CRYPTO EXCHANGESFINSTATE INVESTMENTHOW TO SELL ON CRYPTO COM
As a part of the MeghRaj initiative, MeitY came out with the ‘Cloud First’ policy under which all the departments are required to assess and adopt Cloud computing for their current as well as new applications. To further enhance this adoption, MeitY also empanelled Cloud Service Offerings of private Cloud Service Providers (CSPs) which could be availed by the Government Departments under this initiative.
The focus of the Cloud First policy is to enable Government Departments to deliver both internal function and citizen centric services by leveraging Cloud making Cloud the default option. In case the Cloud is not a feasible option, the Government departments would need to get approval internally by the competent authority for choosing the traditional approach.
By leveraging Cloud, the Government Departments would be able to optimally use IT infrastructure leading to optimal spending on IT procurement, but this would also help them on focusing the core services of the respective department.
Cloud enables Government Departments to procure tools and technologies which are not feasible and viable to procure as a part of standard IT procurement. Every Government Department should adopt a ‘Cloud-by-Default’ approach when designing a new IT service/ application or migrating or enhancing an existing application to reap both financial and non-financial benefits of Cloud.
OPPORTUNITY ONE GROUP SCAMMERKD5 CRYPTO MINERCAN YOU TRADE CRYPTO STOCKS IN MOO MOO
Migration of IT Infrastructure to Cloud is the process of moving application data and platform to the Cloud environment. Depending on the organization requirement(s), the possibility of migration can be from an On-Premises environment to a Cloud Service Provider platform (On-premise to Cloud Migration) or from one Cloud Service Provider platform to another Cloud Service Provider platform (Cloud to Cloud Migration).
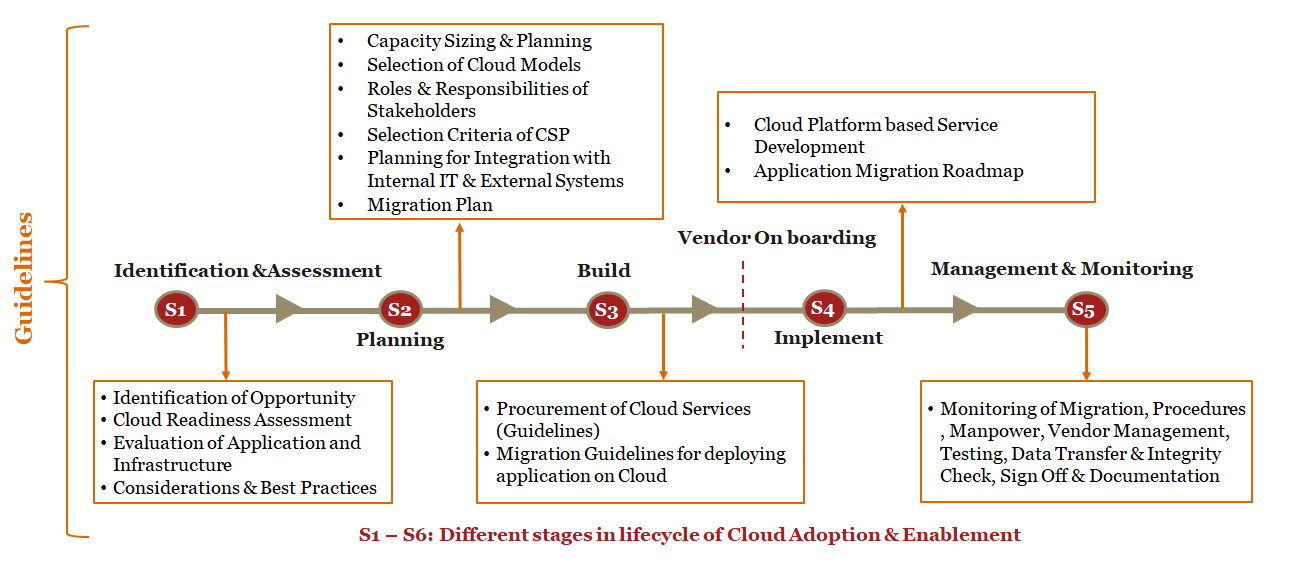
Various stages of Cloud Enablement Lifecycle are:
- i. Identification & Assessment
- ii. Planning
- iii. Build
- iv. Implement
- v. Management & Monitoring
In this phase organization needs to identify their requirements in Cloud and apparently initiate the process to adopt Cloud. By analyzing their business and IT objectives as well as current IT workloads housed either in their own Data Centers, CSP Data Centers, the organizations can identify relevant opportunities that make Cloud adoption essential.
Once the Identification and the Assessment stage has been completed, structured planning is required by the organizations to adopt Cloud, which includes understanding the criteria for evaluating the CSPs, performing the capacity sizing estimation for Compute, Storage and Network and selection of Cloud models suitable for migrating their existing applications.
Once the capacity sizing and selection of suitable Cloud Models has been completed, the organizations should now focus their attention towards the build stage.
Post the completion of Build Stage wherein the procurement has been completed and application has been prepared for migration begins the stage of Implementation. This stage involves preparing the Cloud environment on the CSP platform, installing, and configuring the applications, strengthening the production environment, executing mock migration, final migration and Go-Live to production Cloud. The goal is to ensure all activities are performed in a sequential manner, while minimizing downtime and disruption to users.
This stage includes management & monitoring during and post migration of the applications. The main objective of this stage is to track progress of ongoing migration of different workloads of the organization and performance post migration indicating any operational, performance issues such as data discrepancy. Further, it is also important to manage different application vendors and service providers for achieving a seamless migration. A successful migration is subject to achieving performance improvements and the newly migrated system enabling the organizations to achieve their business objectives.
ERC20地址查询PULLIX CRYPTOSHIB BURNING RATE
The below diagram depicts the stages of the involved in Cloud Enablement and Adoption lifecycle and the guidelines covered under each stage, to enable organizations for evaluation and migration to Cloud Services/ platform procured by them.
Cloud Enablement & Adoption Lifecycle
A holistic and meticulous upfront planning is needed before migrating applications to Cloud. Some common elements of a Cloud migration strategy include evaluating performance and security requirements, calculating costs, and making any necessary departmental changes.
Common challenges an organization faces during a Cloud migration include interoperability, data and application portability, data integrity and security, and business continuity. Without proper planning, a migration could negatively affect workload performance and lead to higher IT costs, thereby negating some of the main benefits of Cloud computing.
سایت کوین مارکت کپHOW DO YOU MAKE MONEY ON COINBASE2 5 LAKH TO USD
With inherent benefits of Cloud being made available to the user Departments it is subsequently important for the user departments to identify their requirements in Cloud and apparently initiate the process to adopt Cloud. By analysing their business and IT objectives as well as current IT workloads housed either in their own Data Centres, CSP Data Centres, the organizations can identify relevant opportunities which make Cloud adoption essential. Following are the potential opportunities to migrate to Cloud.
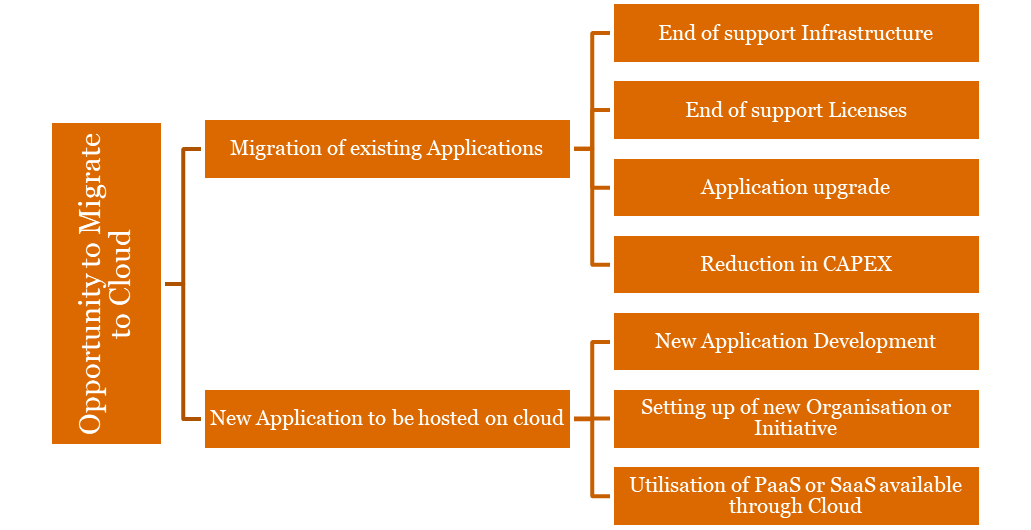
Potential opportunities to migrate to Cloud
BLOCKCHAIN ANALYSISBITCOIN CONFERENCE NASHVILLEECRYPTO1
Some of the indicative factors influencing the adoption of Cloud are as follows:
(i) Reduction in CAPEX: Infrastructure costs gets reduced considerably as the need to purchase expensive equipment and systems, maintenance, and energy consumption costs, gets eliminated. It also reduces delays in service resolutions. Moreover, the pay-as-you-go model is more cost-efficient.
(ii) New Application Development: The Cloud enables greater business agility as it offers a platform for rapid development and deployment of new applications.
(iii) Setting up of new organization or initiative: While planning setup of new IT infrastructure or new department altogether, it is recommended to setup Cloud environment as there are various advantages of opting Cloud over on-premises infrastructure. Some of them are mentioned below:
- a) Business agility: Greater business agility is offered by Cloud as it offers a perfect platform for rapid development, deployment, and experimentation.
- b) Scalability:Cloud adoption makes it easier for organizations to scale up or down according to their operation and storage requirements.
- c) Flexibility: Cloud increases flexibility as Department users can access their data from anywhere. This boosts productivity
- d) Enhanced efficiency: The Cloud environment enhances work efficiency, offering seamless collaboration between various applications.
(iv) End of Support Infrastructure & Licenses: Organizations facing end of support for infrastructure or licenses can opt to move on Cloud environment. These applications can be migrated to Cloud which will help in reducing the overall IT cost.
BITCOIN PRICE AFTER CONFERENCE 2024CRESO CRYPTOMOONBAG CRYPTO
TRADINGVIEW BTCUSDTWHEN IS TRUMP SPEAKING AT THE BITCOIN CONFERENCETESLA CRYPTOCURRENCY
The Existing application needs to be assessed categorically based on certain criteria, as listed below-
- (i) Technical Feasibility Assessment
- (ii) Risk Assessment
- (iii) Strategic Alignment and Cost Assessment
The Technical Feasibility Assessment activity shall help a user Department to analyse its application on dimensions, such as Interdependency (dependency of application on different application, hardware, or platform), sensitivity to network, Horizontal & Vertical Scaling capability, Performance needs, Recovery capabilities, etc. Post performing the Technical Assessment with the guiding questions the user department’s will be able to migrate to Cloud with ease.
Risk Assessment is a key activity when planning to migrate the application on Cloud. Assessing the application across various dimensions, such as geographical location of the data, sensitivity of data, business criticality, the need to protect personal identifiable information (PII) and personal health information (PHI), shall help user departments analyse the risks associated and if the department can migrate its application on Cloud with the risk or if any mitigation plan is required to be formulated to minimize the impact of those risks.
Strategic Alignment and Cost Assessment is another key area for user departments to analyse before migrating its application to Cloud. It is essential to understand for a department which Cloud Deployment Model and Cloud Service Model shall be suitable, the total cost of ownership for migrating to Cloud and running business operations successfully from the chosen Cloud.
FREE BITCOIN MINERSMOKING CRYPTOCRYPTO WASH SALE
The key considerations which may help user Departments to make appropriate and thoughtful decisions before planning the Cloud migration are:
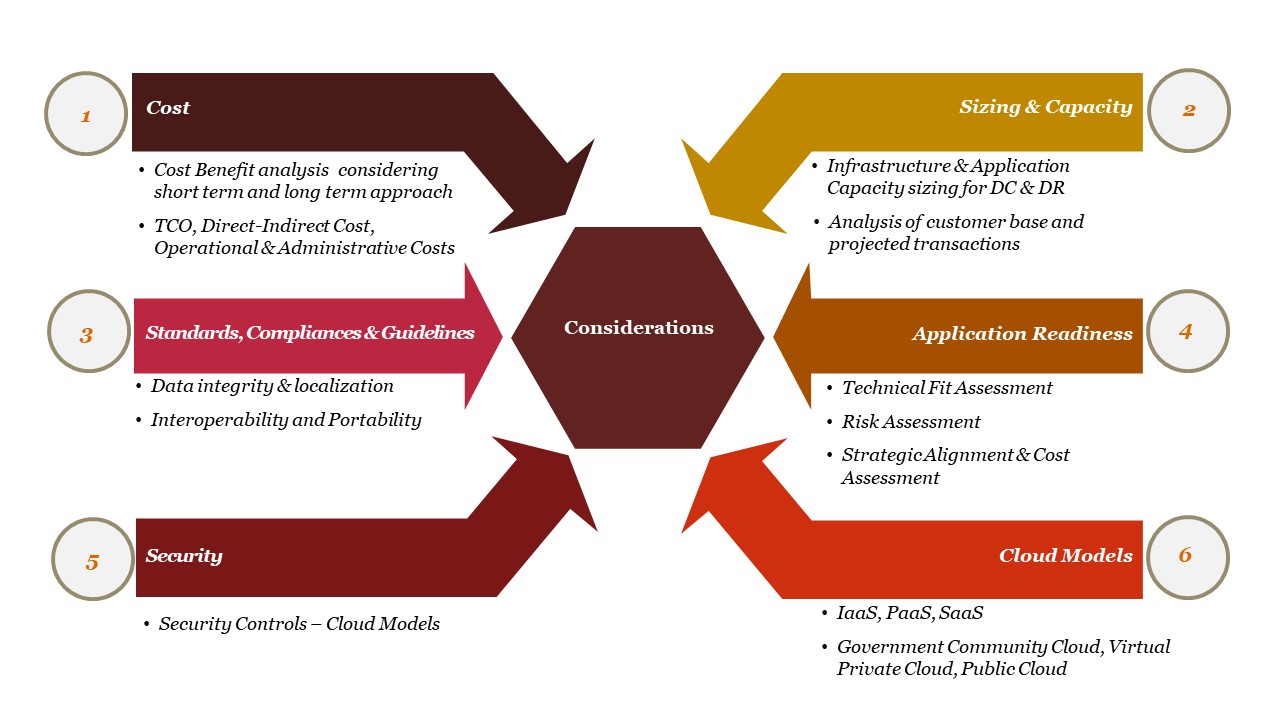
Key Consideration for Cloud Adoption & Migration
(i) Cost: User Departments should adopt a holistic approach while calculating the total cost of migration from on-premises to Cloud environment or from one CSP environment to another CSP environment. While, Cloud offers lower costs, but there are various factors that should be considered such as, direct costs, operational costs, administrative costs and indirect cost. It is also necessary to consider the transition period during which departments will be incurring cost for on-premises data center as well as cloud.
Total Cost of Ownership (TCO) is also one of the important factors that needs to be accounted before planning migration. The calculations for TCO are generally based on the assumption that cloud computing doesn’t require major hardware/software investments upfront and the Departments only pay for the resources they actually use/consume.
(ii) Capacity Sizing: The Capacity Sizing of compute, storage, network, and connectivity require analysis of present utilization of the existing Infrastructure & applications and future growth in terms of transactions and user base. Identifying the optimal resources required in the cloud for each of the workloads shall enable Government Departments to achieve optimal performance requirements and shall allow upsizing and downsizing of resources as per requirement.
(ii) Capacity Sizing: The Capacity Sizing of compute, storage, network, and connectivity require analysis of present utilization of the existing Infrastructure & applications and future growth in terms of transactions and user base. Identifying the optimal resources required in the cloud for each of the workloads shall enable Government Departments to achieve optimal performance requirements and shall allow upsizing and downsizing of resources as per requirement.
(iv) Application Readiness: When the User Departments plan migration to Cloud, a detailed analysis of an application is performed to assess its Cloud readiness. Some of the existing applications may need modernization to take the advantage of the cloud.
(v) Security: Implementation of well-defined security policies & procedures is a must for ensuring adequate security of the applications in the cloud. Migrating infrastructures, services or applications to the cloud without increasing the security overhead requires vigilant preparation & strengthening of security posture. Successful cloud migration requires migrating security to the cloud enabling User Departments to deploy and manage a single, consistent security framework that covers the complete Cloud infrastructure.
(vi) Cloud Models: User Departments must understand how the Cloud architecture and Platform line up with their current environment and see the dependency of components. The evaluation of Cloud Service & Deployment Model is an essential step towards Cloud migration.
BEST CM IN THE WORLD646 BTC TO USDAVT CRYPTO
When departments plan for Cloud migration, various processes and practices may be evaluated during the planning stage for implementing a successful Cloud-migration strategy. Though every Cloud migration event has unique set of requirements, few common best practices help departments in successfully migrating to Cloud.
(i) Data Backup during Migration: While performing application migration it is pertinent to ensure the protection of data. It is proposed that departments always create a full backup of their systems which they plan to migrate before performing the actual migration. Any unexpected event during migration may result in loss of data or unusable application state. Hence, backup gives an extra layer of protection in such events.
(ii) Formulate a properly planned migration strategy: Departments should begin the migration process by mapping out a migration strategy that identifies clear business motives and use cases for moving to the Cloud.
(iii) Manage the software licensing: A major concern for is whether their existing licenses for on-premises software can be extended to Cloud. Hence, Departments can leverage on the Bring Your Own License (BYOL) program that give Departments the flexibility to reuse their licenses on Cloud.
(iv) Prioritize Migration Dependencies: Before migrating to Cloud, during the planning stage it is important to identify the dependency of each component or services and their connections. For the user departments having complex on-premises setups, it is a good practice to understand dependencies of various workloads and prioritize migration of workloads with minimum to maximum dependencies accordingly.
(v) Roles & Responsibilities: Charting out complete Roles & Responsibilities of stakeholders, customized to the Project requirements.
Note: All the aspects in this chapter have been covered in detail in the End-user guide for the adoption of Cloud Services document, available on the MeghRaj webpage of MeitY’s website.
USDT とはQUALIS CRYPTOREDDIT HENRY FINANCE
CRYPTO COM BUY USDT WITH CREDIT CARDSECRET CURRENCY 10HOW MANY SHARES OF ARKK EQUAL 1 BITCOIN
- Security and Privacy: This is the primary concern in adoption of Cloud computing among user departments. Most of the security and privacy risks can be mitigated by implementation of standards and best practices of security such as ISO 27001, ISO 27017 and 27018, ISO 20000-1, PCI-DSS etc. Also, departments should perform the due diligence on the CSP physical region for storing data and virtual servers to mitigate data sovereignty risks. The Data Centre Facility of the CSP shall at minimum implement the security toolset: Security & Data Privacy (Data & Network Security including Anti-Virus, Virtual Firewall, Multi Factor Authentication, VPN, IPS, Log Analyzer / Syslog, SSL, DDoS Protection, HIDS / NIDS, Rights Management, SIEM, Integrated Vulnerability Assessment, SOC, Private Virtual Zones, Data Privacy, Data Encryption, Certifications & Compliance, Authentication & Authorization, and Auditing & Accounting). CSPs shall also ensure that they meet the ever-evolving security requirements as specified by CERT-In (http://www.cert-in.org.in/). User departments should also retain the control and ownership of their data and implement required access controls, policies and procedures to meet the their internal IS requirements.
- Interoperability and Portability: User departments should have the ability to migrate from one Cloud provider to another CSP. This would reduce the risk of vendor lock-in and provide flexibility for switching applications and data from one CSP to other.
- Reliability and Availability: While the natural capability of Cloud is to have near 100% reliability and availability, there have been cases of power failure and other acts of God that shutdown the services. User departments should evaluate the SLAs for durability and availability and validate the redundancy level of CSP before selecting a CSP.
- Regulatory Compliance: User departments should consider that the CSP is accredited with valid certifications like ISO 27001, ISO 27017, ISO 27018, ISO 20000-1, SOC1, SOC2, SOC3, etc., to address the regulatory requirements. CSPs offering services in India should also adhere to CERT-IN & MeitY recommendations on Cloud that includes physical isolation and data residency within Indian borders.
- Performance: Departments should evaluate performance from network, application, and data retrieval aspects. Network is a key component to access resources in public Cloud. A detailed evaluation of application data flow (end-to-end) may be required to identify the right candidate for Cloud-based deployment to ensure the desired performance.
CRYPTO ARENA EVENTS CALENDARCOINBASE RIDDLE ANSWERS TODAYHOW TO GET FREE BITCOINS INSTANTLY
Security in the Cloud is a shared responsibility between user departments and CSPs. Hence, it is important to understand the responsibility. Certain security concerns have been listed below:
- Data Breaches: Though Cloud computing services are new and critical, yet data breaches in all forms have existed for decades. One of the main questions which generally Government Departments come across is “With department’s sensitive data being stored online rather than on premise, is the Cloud safe?” Cloud would provide the User Departments with enhanced security measures and necessary certifications. As per the MeitY empanelment of Cloud Service Provider (CSP), all CSPs enforce security controls as per ISO 27001, 27017 etc. but due to nonenforcement of security policies by the Government Department users it may lead to data breaches.
- Improper Cloud Account Management: The development and execution of the Cloud in many organizations has opened a whole new set of issues in account attacks and hijackings. Attackers now can use the department’s Cloud login accounts information to remotely access critical/sensitive data stored on the platform / Cloud; additionally, attackers can misrepresent and manipulate information through hijacked credentials. Hence appropriate Cloud account management methodologies need to be implemented. In some cases, a Managed Service Provider (MSP) may also have access to Government Department Cloud account hence appropriate controls should be implemented for such a condition as well.
- Insider Threat: An intrusion in Government department may seem unlikely, but the insider threat does exist. Government Department’s users can use their authorized access to department’s Cloud-based services to misuse or access information such as citizen information, financial information, and other sensitive information. Hence it becomes imperative for Government Departments to implement a secure strategy for their Cloud implementation and access and ensure that proper access control mechanism is in place to avoid security issues.
- Regulatory Compliance: Data that is perceived to be secure in one country may not be perceived as secure in another country or region. Hence data ownership and governance become important factors while choosing Cloud. As per MeitY’s empanelment all empanelled Cloud Service Provider would be offering Cloud services out of Indian Data Centre facilities and ensure data residency within the country. Data ownership resides with the Government Department.
- Insecure APIs: Application Programming Interfaces (API) give operators the opportunity to customize their Cloud platform. Even though APIs give users the ability to customize features of their Cloud services to suffice the needs, but they also affect encryption, authentication, and provision for access / controls. The growth of APIs provides better services and do increase security risks. APIs give programmers the gears to build their programs to integrate their applications. The vulnerability of an API lies in the communication that takes place between applications. They also originate an opportunity for exploitable security risks.
- Denial of Service Attacks: Unlike other kinds of cyberattacks, which are launched to establish a foothold and extract sensitive information over a longer span of time, denial-of-service attacks do not attempt to just breach the security perimeter. Rather, they attempt to make the services and servers unavailable to Department’s legitimate users. In certain cases, DoS is also used as a cover for malicious activities and directed attack to take down security appliances such as WAF (Web Application Firewalls).
- Insufficient Due Diligence: The issues listed above are technical in nature, however this particular security gap occurs when a Government Department doesn’t have a clear path for its resources and policies for the Cloud. Due diligence for controls internal to Cloud services need to be monitored by the Government Departments. There are multiple service parameters which need to be configured in a manner that they may not lead to operational, reputational or compliance issues. Insufficient due diligence may pose a major security risk when a Government Department overlooks certain Cloud configurations at the user level.
- Shared Responsibilities: Cloud security is a shared responsibility between the Cloud Service Provider and the Cloud consumer. This collaboration between consumer and provider requires the consumer to take necessary actions to protect their data. While major global Cloud Service Providers do have standardized procedures to secure their side, fine grain controls are up to the consumers.
- Data Loss: Data on Cloud platform can be lost through a natural disaster, data deletion or malicious attack by the service provider. Losing critical data / information can be devastating to businesses without a recovery plan.
- Data Breaches: Though Cloud computing services are new and critical, yet data breaches in all forms have existed for decades. One of the main questions which generally Government Departments come across is “With department’s sensitive data being stored online rather than on premise, is the Cloud safe?” Cloud would provide the User Departments with enhanced security measures and necessary certifications. As per the MeitY empanelment of Cloud Service Provider (CSP), all CSPs enforce security controls as per ISO 27001, 27017 etc. but due to nonenforcement of security policies by the Government Department users it may lead to data breaches.
- Improper Cloud Account Management: The development and execution of the Cloud in many organizations has opened a whole new set of issues in account attacks and hijackings. Attackers now can use the department’s Cloud login accounts information to remotely access critical/sensitive data stored on the platform / Cloud; additionally, attackers can misrepresent and manipulate information through hijacked credentials. Hence appropriate Cloud account management methodologies need to be implemented. In some cases, a Managed Service Provider (MSP) may also have access to Government Department Cloud account hence appropriate controls should be implemented for such a condition as well.
- Insider Threat: An intrusion in Government department may seem unlikely, but the insider threat does exist. Government Department’s users can use their authorized access to department’s Cloud-based services to misuse or access information such as citizen information, financial information, and other sensitive information. Hence it becomes imperative for Government Departments to implement a secure strategy for their Cloud implementation and access and ensure that proper access control mechanism is in place to avoid security issues.
- Regulatory Compliance: Data that is perceived to be secure in one country may not be perceived as secure in another country or region. Hence data ownership and governance become important factors while choosing Cloud. As per MeitY’s empanelment all empanelled Cloud Service Provider would be offering Cloud services out of Indian Data Centre facilities and ensure data residency within the country. Data ownership resides with the Government Department.
- Insecure APIs: Application Programming Interfaces (API) give operators the opportunity to customize their Cloud platform. Even though APIs give users the ability to customize features of their Cloud services to suffice the needs, but they also affect encryption, authentication, and provision for access / controls. The growth of APIs provides better services and do increase security risks. APIs give programmers the gears to build their programs to integrate their applications. The vulnerability of an API lies in the communication that takes place between applications. They also originate an opportunity for exploitable security risks.
- Denial of Service Attacks: Unlike other kinds of cyberattacks, which are launched to establish a foothold and extract sensitive information over a longer span of time, denial-of-service attacks do not attempt to just breach the security perimeter. Rather, they attempt to make the services and servers unavailable to Department’s legitimate users. In certain cases, DoS is also used as a cover for malicious activities and directed attack to take down security appliances such as WAF (Web Application Firewalls).
- Insufficient Due Diligence: The issues listed above are technical in nature, however this particular security gap occurs when a Government Department doesn’t have a clear path for its resources and policies for the Cloud. Due diligence for controls internal to Cloud services need to be monitored by the Government Departments. There are multiple service parameters which need to be configured in a manner that they may not lead to operational, reputational or compliance issues. Insufficient due diligence may pose a major security risk when a Government Department overlooks certain Cloud configurations at the user level.
- Shared Responsibilities: Cloud security is a shared responsibility between the Cloud Service Provider and the Cloud consumer. This collaboration between consumer and provider requires the consumer to take necessary actions to protect their data. While major global Cloud Service Providers do have standardized procedures to secure their side, fine grain controls are up to the consumers.
- Data Loss: Data on Cloud platform can be lost through a natural disaster, data deletion or malicious attack by the service provider. Losing critical data / information can be devastating to businesses without a recovery plan.
The Open Web Application Security Project (OWASP) has additionally listed certain Cloud Security concerns such as User Identity Federation, Business Continuity and Resilience, Service and Data integration, Multi-tenancy and Physical security, Infrastructure Security which have been addressed in the requirements laid down as a part of empanelment of Cloud Service Providers by MeitY (refer Empanelment of Cloud Service Providers (CSPs) https://meity.gov.in/content/gi-Cloud-meghraj).These requirements make CSPs accountable for their responsibilities towards Cloud security.
PIXELS CRYPTOSOURCES KAMALA COINBASE RIPPLE LABSTIMESCRYPTO DAY TRADING PLATFORM
The security design principles are the key pillars for adoption and implementation of Cloud Security to protect system, application, and platform to improve overall security architecture.
Below are the key design principles which needs to be considered for Cloud technology adoption:
- 1 . Security at all layers: Ensure robust Security is applied to all layers (Physical, network, Data, Application, etc.) of their architecture with multiple security controls. This will ensure end to end protecting of application/data hosted by departments on Cloud platform.
- 2. Safeguard data while at rest and in transit: Identify and Classify the data in terms of criticality/sensitivity and define their levels. This can be prevented via using the available security controls like access control, tokenization, encryption, etc.
- 3. Monitoring and Auditing: Ensure monitoring, auditing, and alerting is configured to capture the changes in the department’s system in real time. Further, log integration and metric collection can automatically investigate, act, and respond.
- 4. Access management and Controls: Ensure implementation of principle of selective privileges and impose segregation of duties with appropriate access and authorization. Centralized identity and access management can eliminate any unauthorized access and information loss/theft.
- 5. Readiness for security events: Department/CSP needs to prepare system for any unusual security event. Regular vulnerability and security tests need to be conducted to identify the security gaps and issues. Several drill can be conducted to record the response of the Cloud systems at different layers.
- 6. Automate security best practices: Automating software/hardware/Application based security system via AI/ML/Bots to improve the ability to secure environment which can perform regular checks and implement the controls needed to restrict the attack and enhance Cloud security.
- 7. Cloud Vendor Lock-in: Departments to ensure that there is no vendor lock-in by Cloud services provider while hosting the application/data, as there is no standard guidelines between different Cloud providers for data migration and exports, so it becomes difficult to migrate data from one Cloud provider to another or migration to on-premise Data centre.
HOW MUCH DO SHIBA INUS COSTWHEN IS NASHVILLE BITCOIN CONFERENCECOINBASE APAC
When moving an application/data to the Cloud, user departments should review their security posture and identify changes and controls that need to be implemented to operate securely. Departments should perform static and runtime code analysis of the application before/after deployment in the Cloud.
When using CSPs, departments should retain control and ownership of their data and should implement required security controls to meet internal and external security requirements. They can also consider using other data protection technologies like masking/encryption while moving giving due consideration to performance snags/delays.
Security in the Cloud depends on many factors like whether one choose SaaS, PaaS, or IaaS, and whether the Cloud is private, public, hybrid or community based.
BINANCE ORDIBITCOIN EVOLUTIONWILL CITI LET U BUY CRYPTO WITH CREDIT CARD
The security aspects of Cloud computing are categorized as:
- Infrastructure Security: The first level of security needed is at physical level, to ensure that Cloud datacenters and compute, storage and network resources are physically secure. The security of the infrastructure and provisioning of secured environmental conditions is a basic requirement.
- Network Security: In public Cloud, security considerations increase multi-fold with respect to connectivity to Cloud, security policies to be enforced to mitigate risks associated in data transfer to or from Cloud. It is very important to optimize service availability by mitigating risks to network components. Availability and performance of network links is necessary for ensuring that resources in Cloud are accessible from within the organization and outside.
- Application and Platform Security: It is very essential to keep applications secure and protected from malicious and fraudulent use. Applications does face threat from vulnerabilities and other techniques include (but are not limited to) cross-site scripting, SQL injection and code hacking, and malicious users trying to scan applications to exploit vulnerabilities. A CSP should have effective measures in place to deal with such threat and provide protection as a service offering or enable user departments to use other third-party solution to mitigate these risks.
- Data Security: All sensitive or regulated data needs to be protected in Cloud including archived data. User departments should be able to put in place controls to prevent compromising data by accidental deletion or alteration and have backup of data to recover in case of unfortunate incident. In the case of data, which is protected using encryption, the loss of encryption key poses a definite threat to the consumers.
BITGET DEFINITIONCRYPTO ICONBITCOIN DEPOT GOOGLE BBB REVIEWS
Cloud Security Alliance (CSA) is a non-profit organization working on a wide range of initiatives in Cloud security. For example, CSA publishes a free guide and instructions on Cloud security. Members of CSA include CSPs, vendors, corporate users, academicians of Cloud computing, in addition to individuals. That combination gives a good weight behind the association and its initiatives. Other initiatives from CSA includes a GRC stack with a “control matrix”. The matrix has a series of “controls” with relevance to Cloud security, each mapped up to ISO 27001, PCI, COBIT, NIST and more. CSA also offers a certification programme-CCSK on Cloud Security.
Like CSA, there are also other organizations such as Cloud Standards Customer Council and IEEE that are focused on Cloud Standards. Cloud Computing Innovation Council of India (CCICI) is another collaborative organization with experts from industry and researchers to promote Cloud standards and adoption models.
HOW2 INVEST COM BITCOINEURETHIUMETHEREUM ETF TRADING DATE
The most common method of authentication is password protected. However, service providers offer higher reliability, more powerful tools, such as certificates and tokens to their customers. CSPs should also support standards like LDAP and SAML for identification and authorization. Also, CSP should provide Multi-Factored Authentication for accessing the VMs.
ALI MARTINEZ CRYPTOETHEREUM FOUNDATION UNDER INVESTIGATION1 USDT TO USD
Protecting data in Cloud environment is key and is achieved by using the right encryption mechanism for protecting both data at rest and data in transit.
Data in Transit: User department can use both IPSec and SSL/TLS for protection of data in transit. IPSec is a protocol that extends the IP protocol stack, often in network infrastructure, and allows applications on upper layers to communicate securely without modification. SSL/TLS, on the other hand, operates at the session layer. There are third-party SSL/TLS wrappers.
Data at Rest: User departments should use AES-256/PGP bit encryption for data at rest and consider using key management for securing access to encryption keys. Department should also check if CSP is supporting Client-side encryption. In this approach, data is encrypted before sending to CSP.
PRIME CRYPTO PRICECOINBASE HISTORYCHEAPEST WAY TO BUY BITCOIN
For a user department migrating to Cloud it is imperative to observe security discipline at various levels which ensures a secure adoption of Cloud. IT security encompasses the lowest layers of security, from physical facilities through the Department’s configuration and implementation of IT infrastructure components. These are the fundamental components that everything else in the Cloud is built from, including compute (workload), networking, and storage security.
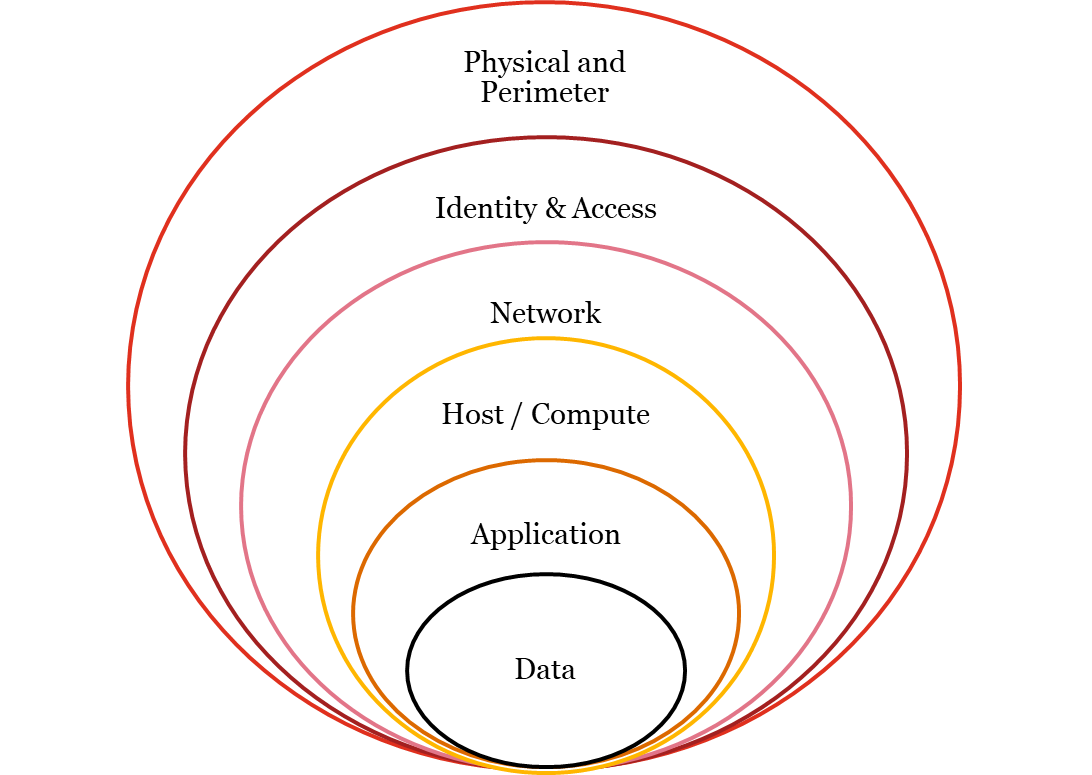
Layered approach towards Security
It is important to know about the infrastructure security parameters of the Cloud service provider. In the shared security model, the provider (or whoever maintains the private Cloud platform) has the burden of ensuring the underlying physical, abstraction, and orchestration layers of the Cloud are secure.
CRYPTO ARENA JOB OPPORTUNITIESPNG CRYPTO PRICEPEPE ON ETHEREUM
Departments may adopt certain practices around data protection in order to overcome any reluctance around data security in Cloud.
- Department need to be aware of the type of data being handled by them and hence they at their discretion may categorize and deploy relevant data on Cloud.
- Departments should adopt a data usage policy which clearly outlines various data access types, who has access to data and what conditions may constitute correct usage of data. There should be safeguards for policy violations and subsequent impact-based consequences.
- Access control is one of the most crucial aspects of data protection in Cloud wherein Departments would be responsible for ensuring Administrative and Technical Controls to manage access to data on the Cloud.
- The CSP shall be responsible for ensuring Physical Security of the deployed Cloud infrastructure. Some of the practices around data security in Cloud have been captured in this section.
COINBASE VALUATIONMINING DOGECOINKCS PRICE
Applications are hosted on independent virtual machines. Applications/ Sensitive data are more vulnerable in cloud-platforms, as cloud environments are hosted on shared resources. So, special security measure / controls are required to safeguard the client environments.
Some of the key considerations are:
- Build security into the initial application design process. Creating Cloud Native applications presents an opportunity to engage Cloud-based security early.
- Integrate security testing into the deployment process.
- Application integration and information exchange to happen over secured API channels.
- Departments should understand the new architectural options and services available in the Cloud. The departments should update their security policies and standards to support them and shouldn’t merely attempt to enforce existing standards entirely on model.
- Segregation: Web facing application should be deployed in DMZ (De-militarized) zone and the Database Server should be deployed in the secured zone while deploying the application on Cloud.
- Log and monitor API calls.
- Use software-defined security to automate security controls.
- Use event-driven security such Anti-virus, when available, to automate detection and remediation of security issues.
BUYING A CAR WITH BITCOINNASDAQ:COIN FINANCIALSШИБА ИНУ
Some of the key practices are:
- Implement appropriate role-based access controls and strong authentication for all Virtual Machines (VM), Containers and VM images.
- Disable remote access post application configuration.
- Integrate security testing and policies while VM image creation.
- Employ the use of pre-certified VM images from the Cloud platform where pre-certification would be an on-going effort.
- Prefer use of file integrity monitoring in order to ensure authenticated changes and detect unapproved changes to files.
- Ensure Operating System Hardening is performed on the virtual machine.
- Prefer Patching of VM images rather than patching running instances. Ensure patching is up to date for Operating System, Database licenses etc.
- Store logs external to workloads.
- Perform periodic vulnerability assessments and penetration testing (VAPT) on Department’s Cloud infrastructure.
- For critical workloads ensure High Availability at all deployment levels – compute, firewall, Load balancers.
- In case of Business-Critical Applications plan for Disaster Recovery (DR).
- Ensure VM level encryption through Bitlocker, LUKS etc. for security of VM in case of compromise
- Install Anti-virus software on Virtual Machine and ensuring periodic patching is performed.
- Take periodic VM snapshots and save in a secured repository.
- Departments should ensure that as soon as the new application server is deployed, security scans should be enabled, and the servers should be added to continuous monitoring.
CHINESE CRYPTOELON MUSK BITCOIN GIVEAWAYCASH APP GLITCH BITCOIN TODAY
There are various kinds of virtual networks, from basic VLANs to full Software-Defined Networks (SDNs). The data in transit also needs to secure through the network layer. A cloud service provider needs to understand the department network traffic plan to send and receive data. Department to ensure CSP has implemented strong security controls for internal and external network separation / communication. CSP to ensure appropriate network segmentation which separates networks of different sensitivity levels
Some of the key points to consider are:
- Use Virtual Private Network (SSL or Site to Site) to access Cloud infrastructure and services
- Use IP Whitelisting to allow connections from certain IPs and deny all others where applicable
- Pre-certifying additional VLAN, firewall ports and load balancers.
- Prefer use of SDN capabilities for multiple virtual networks and multiple Cloud accounts/segments to increase network isolation.
- Separate Cloud accounts and virtual networks reduce security risks compared to traditional data centers.
- Always restrict traffic between workloads in the same virtual subnet using a firewall policy whenever possible.
- Minimize dependency on virtual appliances that restrict elasticity or cause performance bottlenecks.
- Regularly monitor network traffic logs or implement a SIEM to get real-time security alerts generated by application and network devices.
- Implement internal security controls and policies to prevent both modification of consumer networks and monitoring of traffic without approval or outside contractual agreements
- Departments should ensure that all new network segments should be registered security scans on deployment and then should be added to continuous monitoring.
- For Department computers connected in a network, refrain from disabling any personal firewalls on the computers.
- An automated response to attacks should be configured and additional information on the intrusion must be acquired. IP blocking, connection termination and signature analysis are some of the processes under such an automated response.
LEVERAGE CALCULATOR CRYPTOBITCOIN AND ETHEREUM NBETTERMENTCRYPTO CASINOS USA
Identity and Access Management (IAM) refers to defining and managing access privileges of individual network users, along with the circumstances in which users are permitted (or forbidden) those privileges. These users may either be external to the Department (e.g. citizens) or internal to the Department (e.g. employees).
Some of the key points to consider are:
- Department to adopt Identity-as-a-Service (IDaaS) for implementation of single sign-on.
- Department and CSP to restrict the use of root and generic accounts for Cloud Management and operations.
- Departments to Adopt a role-per-group model for access of systems.
- Department to ensure resource-level access controls to access Web, Application and cloud resources.
- Implementation of Multi-factor authentication and separate Cloud Accounts.
- Departments to govern the user details and their access levels, periodically.
ETHERCANWITHDRAW BITCOINSMR BEAST BITCOIN
Some of the key practices are:
- Physical Infrastructure and facilities should be held in secure areas – CSP needs to ensure physical and perimeter security are in place to prevent from unauthorized access. This includes having physical entry in controls that ensure access to only authorized personnel for areas containing sensitive infrastructure.
- Protection against external and environmental threats – CSPs to ensure protection against environmental threats including floods, earthquakes, lightning, fire, natural disasters, civil unrest or other threats that could disrupt operations of a data centre.
- Data Centre IT infrastructure security controls – CSP needs to ensure that necessary controls are in place to prevent damage, loss, compromise, or theft of assets.
- Safety against failure of equipment – CSP need to ensure that necessary controls are in place to execute preventive maintenance of all data centre equipment in order to avoid disruption of services due to detectable equipment failures.
- Procedure for data centre asset removal/theft – CSP need to ensure that appropriate controls exist against removal or theft of sensitive assets.
- Safe disposal or reuse of data centre equipment – CSP need to ensure that necessary control are in place for the suitable disposal of any data centre equipment, in particular any devices that might contain important data like storage media.
- Security controls for DC personnel – Suitable controls need to be instituted for all employee working at the facilities of a CSP, including all temporary staff.
- Ensuring Backup, Redundancy and Continuity Plans – CSP needs to provision appropriate mechanism to carry out regular backup of stored data, redundancy of equipment, as well as continuity plans for handling situations leading to equipment failure.
0 1 ETHEREUM TO USDHOW TO RETIRE ON BITCOINZIG CRYPTO
While imbibing the practices around cloud security, User Department may focus on performing some security assessment for their cloud deployment projects. There are certain critical questions which Departments must ask themselves as well as their Cloud Service Providers during each step of security assessment are:
|
Security Step |
Guiding Questions for Security Assessment |
|
Ensuring Governance, Risk and Compliance processes exist |
|
|
Auditing and Reporting |
|
|
Managing People, Roles and Identities |
|
|
Ensuring Data and Information Protection |
|
|
Privacy Policies |
|
|
Assessing security for cloud applications |
|
|
Ensuring Cloud Network security |
|
|
Ensuring controls for physical infrastructure security |
|
|
Managing security terms in cloud service agreements |
|
|
Understanding security requirement in exit process |
|
Guiding Questions for Security Assessment
COINBASE PROMO CODEHOW TO GET A NEW BITCOIN ADDRESS ON CASH APPNASHVILLE BITCOIN CONVENTION
Some of the internationally recognized information security standards are given below:
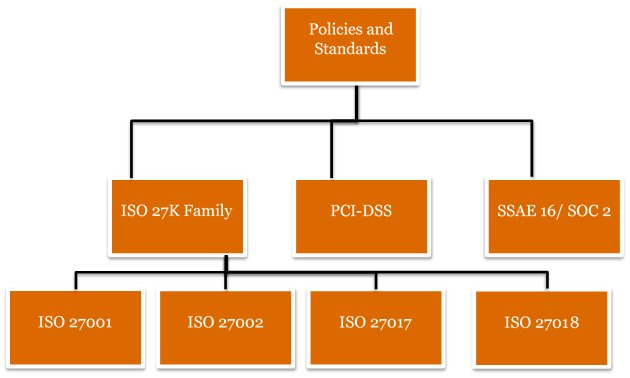
Standards in Information and Cloud Security
ISO/ IEC 27000 Family of Information Security Management System
- ISO 27001: This standard provides best practice to an Information Security Management System (ISMS). This Management System Standard is designed to manage an organizations sensitive data along with its set policies and procedures.
- ISO 27002: ISO 27002 Standard is all about the guidelines for organizational Information Security Management System (ISMS) practices including the selection, implementation and management of controls taking into considerations the organization Information Security Risk environment.
- ISO 27017: ISO 270017 is designed to assist in implementation of controls for cloud-based organizations. This standard is relevant to organizations who store information in the cloud, but also for organizations who provide cloud-based services to other organizations who may have sensitive information.
- ISO 27018: ISO 27018 is for cloud computing organization, specifically designed to protect Personally Identifiable Information (PII) stored and/or processed in the cloud. The primary focus of this standard is relevant to cloud providers and not cloud consumers. This standard gives additional level of confidence to consumers, specifically when working with organizations who handle sensitive information
PCI DSS
Cloud security is a shared responsibility between the cloud service provider (CSP) and its clients. If payment card data is stored, processed or transmitted in a cloud environment, PCI DSS will apply to that environment, and will typically involve validation of both the CSP’s infrastructure and the client’s usage of that environment.
Sector specific standards
- SSAE 16/ SOC 2: Statements on Standards for Attestation Engagements No. 16. SSAE 16 requires Data Center organizations, to provide written report that describes controls at organizations that provide services to customers.
- SOC 2 is a report which focuses on controls at service provider relevant to security, processing integrity, availability, confidentiality and privacy of a system. It ensures customers that their data is kept private and secure while in storage and in transit and which is available for the customer to access at any time.
HOW TO RETIRE ON BITCOIN22 MILLION WON TO USDHOW TO WITHDRAW IN BINANCE
Securing hybrid IT environments spread across multiple clouds is a complex and challenging task. User Departments planning to operate a mix of on-premise and cloud systems would believe the hybrid environment is actually more secure than the exclusively in-house systems they would be running. Hence improved security would act as a key driver for increasing their use of the hybrid or multi-cloud services.
Multicloud is the use of multiple cloud computing and storage services in a single heterogeneous architecture. This also refers to the distribution of cloud assets, software, applications, etc. across several cloud-hosting environments. With a typical multicloud architecture utilizing two or more public clouds as well as multiple private clouds, a multicloud environment aims to eliminate the reliance on any single cloud provider.
Protecting the cloud infrastructure is incumbent on the cloud service provider, but it’s the Government Department’s responsibility to protect any data it puts into the cloud. So ultimately, it’s down to User Department to carry out due diligence when selecting CSPs/MSPs in order to ensure they meet their security and regulatory requirements.
Certain measures which may be kept in mind while considering a multi-cloud deployment/ environment are as follows:
- Centralize Department’s security strategy
- Evolve the approach to multi-cloud security
- Secure the communications that practically run the applications
- Ensure that your Department employee’s follow security protocol
To identify threats across multiple cloud platforms and effectively integrate security strategies that address the needs of each of these platforms, department’s internal security teams or managed service providers need to centralize security control to maximize data visibility within the multi-cloud environment. Information about all security measures and tools implemented need to be shared across points of contacts responsible for each platform to improve the department’s security capabilities and awareness. Having a uniform protocol for security enforcement ensures a consistent approach to cloud platforms, facilitating the secure integration of a multi-cloud architecture. Automation using third-party services may help in scaling security.
While the Departments ensure that the applications are up to date, it is also important to ensure that the security functions are constantly upgraded to meet the ever-changing landscape. In today’s world, Cyber-attackers are continuously looking for vulnerabilities to exploit and adopting innovative ways to breaching security. Monitoring threats to a multi-cloud architecture is a continuous process that requires security experts to constantly analyze the security of the multi-cloud through real-time reports.
Even if the communications between applications in the multi-cloud and within the applications themselves are secured, many Departments may neglect to secure the communications that control how the applications are run. This is known as the control plane, and a good multi-cloud security strategy should take into consideration the need to encrypt communications that fall within the domain of the control plane. Department’s security teams need to ensure that communications that control virtual machines and containers are encrypted. Often, these communications within the control plane are left unsecured, allowing malicious entities to exploit these weak spots and orchestrate a serious security breach.
One of the biggest security breaches would involve scenarios where individuals would have access to data and services that they should not be able to view. When unrelated people are allowed access to sensitive data, they are at risk of exposing the data to cyberattacks and breaches. In such a scenario, Departments need to ensure that any acquired software is patched and secured before rolling it out to employees and that employees are trained to adhere to stringent security protocols to prevent a breach from occurring.
BITCOIN KAUFENHOW DO I CASH OUT FROM COINBASEWHY DID THEY MAKE SO MANY SHIBA INU COINS
Security in Cloud Computing follows the shared responsibility model. The Cloud Service Provider will always be responsible for securing the physical infrastructure and the virtualization platform itself. Meanwhile, the Cloud consumer i.e. the Government Department, is responsible for properly implementing the available security controls and understanding the underlying risks. For example, deciding when to encrypt virtualized storage, properly configuring the virtual network and firewalls, or deciding when to use dedicated hosting vs. a shared host.
In continuation to the practices around cloud security, certain additional pointers which Government Department should regularly monitor, through audits, for their cloud deployments on parameters such as MFA, data encryption, updates for the running operating system, usage of anti-malware and security tools among others.
Both, the CSP and the Cloud consumer, have certain areas of responsibility for maintaining security in the cloud, and in few domains the responsibility even overlaps. In today’s scenario, many security problems among Cloud consumers involve misunderstanding these shared responsibility areas. User Departments who understand the basic delineation of responsibility are in a much better position to maintain a high level of Cloud security.
Essentially, the CSP requires to ensure that the infrastructure built within their platform, is inherently robust and secure. On the other side, certain customizable Cloud capabilities including network configuration, account access, application management, compute configuration, and data encryption are the responsibility areas of the Cloud consumer.
BEST CRYPTO POKER SITESCRYPTO SAVY TWITTERCRYPTO FLASH LOAN
Risk Assessment is a key activity when planning to migrate the application on Cloud. Assessing the application across various dimensions, such as geographical location of the data, sensitivity of data, business criticality, the need to protect personal identifiable information (PII) and personal health information (PHI), shall help a user department analyse the risks associated and if the department can migrate its application on Cloud with the risk or if any mitigation plan is required to be formulated to minimize the impact of those risks. The various dimensions along which risk to be measured with its description are given below:
- Cross Border Data/ Jurisdiction: The geographic path and location of the data managed by the application. The data should be hosted within Country / jurisdiction. Data crossing international borders is subject to specific laws as defined by Government of India.
- Regulated Data: The need to protect sensitive data from unauthorized disclosure, fraud, waste, or misuse (e.g. Government Financial Records, Sensitive Intellectual Property) Data regulated by specific country regulations such as Outsourcing of Business Activities, Functions and Processes.
- Application Criticality / Availability: An application that is essential to supporting the core business processes of a Government Department. A failure or disruption of application may result in the failure of business operations or serious impact on the services offered by the Government Department.
- PII/PHI Data: PII and PHI data is one of the most sensitive forms of data. It is essential for a Government Department to protect The Personally Identifiable Information (PII) and Protected Health Information (PHI) from unauthorized disclosure, fraud or misuse.
- Reputation Impact: Negative impact on the reputation of a Government Department and its identity due to the failure of a 3rd party to provide the contracted services which were essential for citizens. (Primarily applies for citizen centric applications).
- Licensing: It defines the licensing requirement of a Government Department. Different Middleware, Database, Backup license(s) etc. might be required to run the applications. Licenses may be restricted in use based on CPU, virtualized hosts, concurrent users, ability to transfer, etc. (Licensing policy).
Note: All the aspects of Cloud security are covered in detail in the Cloud Security Best Practices document, available on the MeghRaj webpage of MeitY’s website.
Contact Us
SEI CRYPTO PRICE PREDICTION
(Government of India)
AMBUD
BITCOIN IMAGE NO BACKGROUND
-
 Hi there üëã
Hi there üëã
How can I help you today?
 More
More